Title: Cyber Threat Mitigation: Safeguarding Your Digital World
Introduction:
In today’s interconnected world, where technology plays a vital role in our daily lives, the looming threat of cyber attacks is a growing concern. Cyber criminals are becoming more sophisticated, targeting individuals, businesses, and even governments. To protect ourselves and our digital assets, it is crucial to understand the concept of cyber threat mitigation.
Understanding Cyber Threats:
Cyber threats encompass a wide range of malicious activities aimed at exploiting vulnerabilities in computer systems and networks. These threats include malware, phishing attacks, ransomware, data breaches, and much more. The consequences can be severe, ranging from financial loss to reputational damage or even compromise of personal or sensitive information.
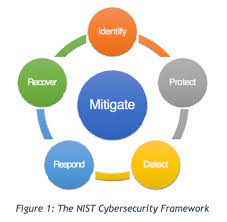
The Importance of Cyber Threat Mitigation:
Cyber threat mitigation refers to the proactive measures taken to minimize the impact of potential cyber attacks. It involves implementing robust security measures that not only detect and prevent threats but also respond effectively if an incident occurs. By adopting a comprehensive approach towards cybersecurity, individuals and organizations can significantly reduce their risk exposure.
Best Practices for Cyber Threat Mitigation:
- Keep Software Up-to-Date: Regularly update operating systems and software applications to patch vulnerabilities that could be exploited by cybercriminals.
- Implement Strong Password Policies: Enforce the use of complex passwords across all accounts and encourage multi-factor authentication for an added layer of security.
- Educate Users: Raise awareness among employees or family members about common cyber threats such as phishing emails or suspicious links. Teach them how to identify potential risks and report any suspicious activity promptly.
- Use Reliable Security Software: Invest in reputable antivirus software that offers real-time protection against malware and other emerging threats.
- Regularly Back Up Data: Create backups of critical files and store them offline or in secure cloud storage platforms to mitigate the impact of ransomware attacks or data breaches.
- Conduct Vulnerability Assessments: Regularly assess your systems and networks for vulnerabilities, and promptly address any identified weaknesses.
- Implement Firewall Protection: Utilize firewalls to monitor and control incoming and outgoing network traffic, acting as a barrier between your devices and potential threats.
- Establish an Incident Response Plan: Prepare a well-defined incident response plan that outlines the steps to be taken in case of a cyber attack. This includes isolating affected systems, notifying relevant parties, and restoring operations efficiently.
Conclusion:
Cyber threat mitigation is an ongoing process that requires constant vigilance and adaptation to the evolving threat landscape. By implementing best practices for cybersecurity, individuals and organizations can significantly reduce their risk exposure. Remember, prevention is always better than cure when it comes to protecting our digital world. Stay informed, stay proactive, and together we can create a safer digital environment for all.
Frequently Asked Questions: Cyber Threat Mitigation in UK
- What are the 3 types of mitigation cybersecurity?
- What are the threat mitigation principles?
- How can we mitigate cybersecurity risk?
- What is cyber threat mitigation?
What are the 3 types of mitigation cybersecurity?
When it comes to cybersecurity mitigation, there are three primary types of approaches that organizations and individuals can employ to minimize the impact of cyber threats:
Preventive Mitigation:
Preventive mitigation focuses on proactively preventing cyber threats from infiltrating systems or networks. This approach involves implementing various security measures to reduce vulnerabilities and deter potential attackers. Examples of preventive measures include:
– Installing and regularly updating antivirus software, firewalls, and intrusion detection systems.
– Enforcing strong password policies and multi-factor authentication.
– Conducting regular software updates and patch management to address known vulnerabilities.
– Implementing secure network configurations and access controls.
– Providing cybersecurity awareness training to educate users about potential threats.
Detective Mitigation:
Detective mitigation aims to identify and detect cyber threats as early as possible. This approach involves deploying monitoring tools and techniques to identify suspicious activities or anomalies within systems or networks. Examples of detective measures include:
– Intrusion detection systems (IDS) that monitor network traffic for signs of unauthorized access or malicious activity.
– Security information and event management (SIEM) systems that collect, analyze, and correlate security event logs from various sources for threat detection.
– Log monitoring and analysis to identify patterns indicative of a potential breach or unauthorized access.
– Regular vulnerability assessments and penetration testing to identify weaknesses before they are exploited.
Corrective Mitigation:
Corrective mitigation focuses on responding promptly and effectively in the event of a cyber attack or security breach. This approach involves taking immediate actions to minimize damage, restore operations, and prevent further compromise. Examples of corrective measures include:
– Incident response planning: Developing a well-defined plan outlining the steps to be taken during a cyber incident, including containment, investigation, recovery, and communication protocols.
– Isolating affected systems or networks from the rest of the infrastructure to prevent further spread of malware or unauthorized access.
– Restoring data from backups after ensuring their integrity.
– Conducting forensic analysis to determine the cause and extent of the attack.
– Implementing additional security measures or patches to prevent similar incidents in the future.
It’s important to note that these three types of mitigation strategies are not mutually exclusive, and a comprehensive cybersecurity approach often combines elements from each category. By employing preventive, detective, and corrective measures, organizations and individuals can enhance their overall cybersecurity posture and better protect their digital assets.
What are the threat mitigation principles?
Threat mitigation principles are a set of guidelines and strategies aimed at reducing the impact and likelihood of cyber threats. These principles serve as a framework for individuals and organizations to develop effective cybersecurity practices. Here are some key threat mitigation principles:
- Risk Assessment: Conduct a comprehensive risk assessment to identify potential vulnerabilities, threats, and their potential impact on your systems, networks, and data. Understanding your specific risks allows you to prioritize mitigation efforts effectively.
- Defense in Depth: Implement multiple layers of security controls across your systems and networks. This approach ensures that if one layer fails, other security measures can still provide protection. It includes using firewalls, intrusion detection systems, access controls, encryption, and regular security updates.
- Least Privilege: Grant users the minimum level of access necessary to perform their tasks effectively. Limiting user privileges reduces the risk of unauthorized access or accidental misuse of sensitive information.
- Continuous Monitoring: Implement monitoring systems that actively track network traffic, log events, and detect anomalies or suspicious activities in real-time. Regularly review logs and security alerts to identify potential threats promptly.
- Patch Management: Establish a robust patch management process to ensure that all software applications, operating systems, and firmware are regularly updated with the latest security patches. Prompt patching helps address known vulnerabilities before they can be exploited by attackers.
- Employee Training and Awareness: Educate employees about cybersecurity best practices, such as recognizing phishing emails, avoiding suspicious links or attachments, and using strong passwords. Regular training sessions help create a culture of security awareness within an organization.
- Incident Response Planning: Develop an incident response plan that outlines the steps to be taken in case of a cyber attack or data breach. This plan should include roles and responsibilities for incident response team members, communication protocols for notifying stakeholders, containment strategies, evidence preservation procedures, and system recovery processes.
- Data Backup and Recovery: Regularly back up critical data and store backups in secure locations, preferably offline or in encrypted cloud storage. This practice ensures that even if data is compromised or lost due to a cyber attack, it can be restored from backups.
- Vendor and Supply Chain Security: Assess the security practices of third-party vendors and suppliers before engaging in business partnerships. Ensure that they have robust security measures in place to protect your shared data and systems.
- Regular Security Audits: Conduct periodic security audits and penetration testing to identify vulnerabilities and weaknesses in your systems. Regular assessments help you stay proactive and address potential risks before they can be exploited.
By following these threat mitigation principles, individuals and organizations can enhance their cybersecurity posture, reduce the risk of cyber threats, and protect their valuable assets from malicious actors.
How can we mitigate cybersecurity risk?
Mitigating cybersecurity risks is crucial to protect our digital assets and sensitive information from potential threats. Here are some effective strategies for mitigating cybersecurity risks:
- Conduct Regular Risk Assessments: Regularly assess your systems, networks, and digital infrastructure to identify vulnerabilities and potential risks. This includes evaluating the effectiveness of existing security measures and identifying areas that require improvement.
- Implement Strong Access Controls: Control access to your systems and data by implementing strong authentication mechanisms such as complex passwords, multi-factor authentication (MFA), and role-based access controls (RBAC). Limiting access to authorized personnel helps prevent unauthorized individuals from gaining entry.
- Keep Software Up-to-Date: Ensure that all software applications, operating systems, and firmware are up-to-date with the latest security patches and updates. Regularly applying patches helps address known vulnerabilities that cybercriminals may exploit.
- Educate Employees: Train employees on cybersecurity best practices, including how to identify phishing emails, how to create strong passwords, and how to handle sensitive information securely. Regular awareness programs can significantly reduce human error-related risks.
- Use Reliable Security Software: Invest in reputable antivirus software, firewalls, intrusion detection systems (IDS), and other security solutions that provide real-time protection against malware, ransomware, and other emerging threats.
- Employ Data Encryption: Encrypt sensitive data both at rest (stored on devices or servers) and in transit (being transmitted over networks). Encryption adds an extra layer of protection by making the data unreadable to unauthorized individuals even if it is intercepted.
- Backup Data Regularly: Implement a robust backup strategy for critical data. Regularly back up your files on separate storage devices or secure cloud platforms so that you can recover them in case of a ransomware attack or data loss incident.
- Monitor Network Activity: Utilize network monitoring tools to detect any suspicious activity or anomalies within your network environment promptly. Proactive monitoring helps identify potential threats and take immediate action to mitigate them.
- Develop an Incident Response Plan: Establish a well-defined incident response plan that outlines the steps to be taken in case of a cybersecurity incident. This includes identifying key personnel, defining communication channels, and outlining the process for containment, eradication, and recovery.
- Regularly Conduct Security Awareness Training: Keep employees updated on emerging cyber threats and provide ongoing training sessions to reinforce good cybersecurity practices. Encourage a culture of security awareness throughout the organization.
By implementing these strategies, organizations can significantly reduce their cybersecurity risks and enhance their overall resilience against potential threats. Remember, cybersecurity is an ongoing effort that requires constant monitoring, adaptation, and improvement to stay ahead of evolving risks.
What is cyber threat mitigation?
Cyber threat mitigation refers to the strategies and actions taken to minimize the impact of potential cyber threats or attacks. It involves a comprehensive approach that aims to detect, prevent, and respond effectively to cyber threats in order to reduce risk exposure.
The goal of cyber threat mitigation is to protect individuals, organizations, and their digital assets from various malicious activities such as malware infections, phishing attacks, data breaches, ransomware, and more. It involves implementing security measures and best practices that help identify vulnerabilities, strengthen defenses, and mitigate the potential consequences of a successful cyber attack.
Cyber threat mitigation includes both proactive and reactive measures. Proactive measures focus on preventing or minimizing the likelihood of an attack by implementing strong security controls, conducting regular vulnerability assessments, educating users about potential risks, keeping software up-to-date with patches and updates, and using reliable security software.
Reactive measures come into play when an incident occurs despite preventive efforts. These measures involve incident response planning and execution. They include isolating affected systems or networks, investigating the incident to determine the scope and impact of the attack, notifying relevant parties such as law enforcement or regulatory authorities if necessary, restoring operations efficiently while minimizing downtime or disruption, and learning from the incident to improve future prevention strategies.
Cyber threat mitigation is an ongoing process due to the constantly evolving nature of cyber threats. It requires continuous monitoring of systems and networks for potential vulnerabilities or suspicious activities. By adopting a proactive mindset towards cybersecurity and implementing effective mitigation strategies, individuals and organizations can significantly reduce their risk exposure and safeguard their digital assets against cyber attacks.