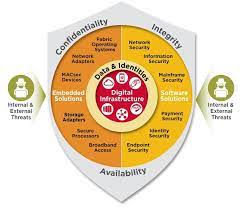
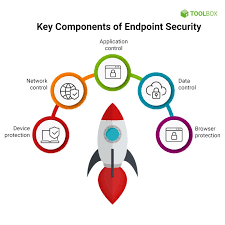
Enhance Your Business’s Security with ESET Endpoint Security: Comprehensive Protection for the Digital Age
ESET Endpoint Security: Protecting Your Business in the Digital Landscape In today's interconnected world, businesses…
0 Comments