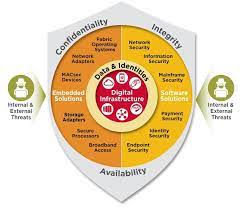
Enterprise Security: Safeguarding Your Business in the Digital Age
In today’s interconnected world, businesses face an ever-growing array of cybersecurity threats. From data breaches to ransomware attacks, the consequences of a security breach can be devastating, both financially and reputationally. This is where enterprise security steps in to protect your business from these evolving threats.
Enterprise security refers to the comprehensive approach that organizations take to safeguard their digital assets, including sensitive data, intellectual property, and customer information. It encompasses a range of strategies and technologies designed to detect, prevent, and respond to cyber threats effectively.
One of the cornerstones of enterprise security is a robust network infrastructure. A secure network forms the foundation for protecting your organization’s digital assets. This includes implementing firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) to create layers of defense against unauthorized access.
Another critical aspect is user authentication and access control. Enterprises must enforce strict policies regarding user access privileges and implement strong authentication methods such as two-factor authentication (2FA) or biometric verification. By ensuring that only authorized personnel can access sensitive information or critical systems, organizations can significantly reduce the risk of internal breaches.
Data encryption is also vital for enterprise security. Encryption converts data into an unreadable format that can only be deciphered with the appropriate decryption key. By encrypting sensitive information both at rest and in transit, businesses can protect their data from being intercepted or compromised by malicious actors.
Regular software updates are crucial for maintaining a secure environment. Organizations should promptly apply patches released by software vendors to address any vulnerabilities that could be exploited by hackers. Additionally, employing advanced endpoint protection solutions helps defend against malware attacks that target individual devices within a network.
Educating employees about cybersecurity best practices is equally important. Human error remains one of the leading causes of security breaches in enterprises. Training programs should cover topics such as identifying phishing emails, creating strong passwords, and recognizing social engineering tactics. By cultivating a culture of security awareness, employees become an integral part of the defense against cyber threats.
Monitoring and incident response are vital components of enterprise security. Implementing security information and event management (SIEM) systems allows organizations to detect and respond to potential threats in real-time. By analyzing network logs, user activity, and system events, businesses can identify anomalies and take immediate action to mitigate risks.
In an ever-evolving threat landscape, enterprises must also stay ahead of emerging risks. This involves conducting regular risk assessments and vulnerability scans to identify any weaknesses in the security infrastructure. By proactively addressing these vulnerabilities, organizations can prevent potential breaches before they occur.
Lastly, maintaining compliance with relevant regulations is essential for enterprise security. Depending on the industry or location, businesses may be subject to specific data protection laws or industry standards. Adhering to these regulations not only helps protect sensitive information but also ensures that your organization avoids legal consequences.
In conclusion, enterprise security is a multifaceted approach that encompasses various strategies and technologies aimed at safeguarding businesses from cyber threats. From network infrastructure and access control to encryption and employee education, each component plays a crucial role in creating a robust defense against potential breaches. By prioritizing enterprise security, organizations can protect their valuable assets, maintain customer trust, and thrive in the digital age.
Frequently Asked Questions: Enterprise Security Measures and Best Practices
- What measures can I take to protect my business from cyber threats?
- How can I ensure the security of my company’s data?
- What steps should I take to secure my business network?
- How do I protect against employee fraud and malicious activity?
- What are the best practices for implementing enterprise security policies?
- How can I stay up-to-date with the latest security technologies and trends?
What measures can I take to protect my business from cyber threats?
Protecting your business from cyber threats requires a comprehensive approach that encompasses both technological and organizational measures. Here are some key steps you can take to enhance your business’s cybersecurity posture:
- Develop a robust cybersecurity policy: Create a clear and comprehensive cybersecurity policy that outlines guidelines, best practices, and expectations for all employees. This policy should cover topics such as password management, acceptable use of technology resources, data handling procedures, and incident reporting protocols.
- Educate employees: Provide regular training and awareness programs to educate your employees about common cyber threats, phishing attacks, social engineering tactics, and safe online practices. Encourage them to be vigilant and report any suspicious activities or potential security breaches promptly.
- Implement strong access controls: Use strong authentication methods such as two-factor authentication (2FA) or biometric verification to ensure that only authorized individuals can access critical systems or sensitive data. Regularly review user access privileges to minimize the risk of unauthorized access.
- Keep software up to date: Regularly update all software applications, operating systems, and firmware on your devices with the latest security patches and updates. Outdated software can contain vulnerabilities that hackers can exploit.
- Use encryption: Encrypt sensitive data both at rest (stored on devices or servers) and in transit (when being transmitted over networks). Encryption helps protect your data from unauthorized access even if it falls into the wrong hands.
- Implement strong password policies: Enforce the use of complex passwords that are unique for each account or system. Encourage the use of password managers to securely store passwords and avoid reusing passwords across multiple accounts.
- Backup important data: Regularly back up critical business data to an offsite location or cloud storage service. This ensures that even if your systems are compromised or experience a ransomware attack, you can restore your data without paying a ransom.
- Use firewalls and antivirus software: Install firewalls at network entry points to monitor and filter incoming and outgoing traffic. Deploy reliable antivirus software to detect and remove malware from your systems.
- Monitor network activity: Implement a security information and event management (SIEM) system or employ intrusion detection/prevention systems (IDS/IPS) to monitor network activity for any suspicious behavior or signs of a potential breach.
- Create an incident response plan: Develop a detailed incident response plan that outlines the steps to be taken in the event of a cybersecurity incident. This includes procedures for containment, investigation, communication, and recovery.
- Regularly assess risks: Conduct regular risk assessments and vulnerability scans to identify any weaknesses in your cybersecurity infrastructure. Address any vulnerabilities promptly to minimize the risk of exploitation by hackers.
- Stay informed: Stay updated on the latest cybersecurity trends, threats, and best practices by following reputable sources such as industry publications, security blogs, and government advisories.
Remember, cybersecurity is an ongoing effort that requires constant vigilance and adaptation. By implementing these measures and regularly reviewing your security practices, you can significantly enhance your business’s resilience against cyber threats.
How can I ensure the security of my company’s data?
Ensuring the security of your company’s data is of utmost importance in today’s digital landscape. Here are some essential steps you can take to enhance data security:
- Conduct a thorough risk assessment: Identify potential vulnerabilities and risks within your organization’s IT infrastructure, including networks, systems, and applications. This assessment will help you understand where your data may be most at risk.
- Implement strong access controls: Control access to sensitive data by implementing strong authentication methods such as multi-factor authentication (MFA) or biometric verification. Limit user privileges to only what is necessary for their roles and regularly review and update access rights.
- Encrypt sensitive data: Utilize encryption techniques to protect sensitive information both at rest (stored on devices or servers) and in transit (being transmitted over networks). Encryption ensures that even if data is compromised, it remains unreadable without the appropriate decryption key.
- Regularly update software and systems: Keep all software, operating systems, and applications up-to-date with the latest patches and security updates. Vulnerabilities in outdated software can be exploited by attackers, so timely updates are crucial for maintaining a secure environment.
- Educate employees on cybersecurity best practices: Human error is a common cause of security breaches. Conduct regular training sessions to educate employees about phishing attacks, social engineering tactics, password hygiene, and other cybersecurity best practices. Encourage them to report any suspicious activities promptly.
- Implement robust backup solutions: Regularly backup your company’s critical data using secure methods such as cloud storage or offline backups. This ensures that even if your primary data is compromised or lost, you can restore it from a reliable source.
- Use firewalls and intrusion detection systems (IDS): Deploy firewalls to monitor incoming and outgoing network traffic and block unauthorized access attempts. IDS systems can detect suspicious activities within your network infrastructure and trigger alerts for immediate action.
- Implement a comprehensive incident response plan: Develop a well-defined plan to respond to security incidents effectively. This includes steps for containment, investigation, recovery, and communication. Regularly test and update the plan to ensure its effectiveness.
- Monitor network and system activity: Implement security information and event management (SIEM) systems to monitor network logs, user activity, and system events in real-time. This enables the detection of potential threats or anomalies promptly.
- Stay informed about emerging threats: Keep up-to-date with the latest cybersecurity trends and threats relevant to your industry. Subscribe to security newsletters, follow reputable cybersecurity blogs, and participate in industry forums to stay informed about emerging risks.
Remember that data security is an ongoing process that requires constant vigilance. By implementing these measures and regularly reviewing your security practices, you can significantly enhance the protection of your company’s valuable data.
What steps should I take to secure my business network?
Securing your business network is crucial to protect your sensitive data and ensure the smooth operation of your organization. Here are some essential steps you should take:
- Conduct a Network Security Assessment: Begin by assessing your network’s current security posture. Identify potential vulnerabilities, weak points, and areas that require improvement. This assessment will serve as a baseline for implementing security measures.
- Implement Firewalls and Intrusion Detection Systems (IDS): Set up firewalls at the network perimeter to filter incoming and outgoing traffic, blocking unauthorized access attempts. Additionally, deploy IDS to monitor network activity and detect any suspicious or malicious behavior.
- Secure Wireless Networks: If you have wireless networks in your organization, ensure they are properly secured with strong encryption (e.g., WPA2 or WPA3). Change default usernames and passwords on wireless routers, use unique SSIDs, and regularly update firmware.
- Use Strong Authentication Methods: Enforce strong password policies across your organization, requiring complex passwords that are regularly changed. Consider implementing two-factor authentication (2FA) or multi-factor authentication (MFA) for an extra layer of security.
- Regularly Update Software and Firmware: Keep all software applications, operating systems, and network devices up to date with the latest patches and security updates provided by vendors. Enable automatic updates whenever possible to ensure timely protection against known vulnerabilities.
- Employ Endpoint Protection: Install robust antivirus/anti-malware software on all devices connected to your business network. Regularly scan for malware, spyware, and other threats to prevent infections that could compromise your network’s security.
- Control User Access Privileges: Implement strict user access controls based on the principle of least privilege (PoLP). Grant employees access only to the resources they need to perform their specific roles within the organization.
- Educate Employees on Cybersecurity Best Practices: Conduct regular training sessions to raise awareness about common cyber threats such as phishing, social engineering, and malware. Teach employees how to identify and report suspicious activities, and encourage a culture of security consciousness.
- Regularly Back Up Data: Implement a robust data backup strategy to ensure that critical business information is regularly backed up and stored securely. Consider using off-site or cloud-based backups for added protection against physical damage or theft.
- Monitor Network Activity: Deploy network monitoring tools to track network traffic, detect anomalies, and identify potential security breaches in real-time. Implement a Security Information and Event Management (SIEM) system to centralize log collection and analysis.
- Create an Incident Response Plan: Develop a comprehensive incident response plan that outlines the steps to be taken in the event of a security breach. This plan should include procedures for containment, investigation, mitigation, and recovery.
- Regularly Test and Update Security Measures: Conduct periodic penetration tests and vulnerability assessments to identify any weaknesses in your network’s security infrastructure. Stay informed about emerging threats and update your security measures accordingly.
Remember that network security is an ongoing process that requires constant vigilance. By following these steps and regularly reviewing your security measures, you can significantly enhance the protection of your business network against cyber threats.
How do I protect against employee fraud and malicious activity?
Protecting against employee fraud and malicious activity requires a combination of preventive measures, monitoring, and swift response. Here are some strategies to help safeguard your business:
- Implement strong internal controls: Establish clear policies and procedures for financial transactions, access to sensitive data, and use of company resources. Enforce segregation of duties to ensure that no single employee has complete control over critical processes.
- Conduct thorough background checks: Before hiring new employees, perform comprehensive background checks to verify their credentials and employment history. This can help identify any red flags or prior incidents that may indicate a higher risk of fraudulent behavior.
- Foster a culture of ethics and transparency: Promote an ethical work environment by setting the right tone at the top. Encourage open communication, provide avenues for reporting suspicious activities anonymously, and ensure that employees understand the consequences of fraudulent behavior.
- Regularly review access privileges: Grant employees access only to the systems and data necessary for their roles. Conduct periodic reviews to ensure that access permissions are appropriate and promptly revoke access for employees who no longer require it.
- Monitor employee activities: Implement monitoring systems to track employee actions on company networks, including logging keystrokes or capturing screenshots when warranted. Monitoring tools can help detect unusual patterns or behaviors that may indicate malicious activity.
- Educate employees about security risks: Provide comprehensive training on cybersecurity best practices, including how to identify phishing emails, avoid social engineering tactics, and protect sensitive information. Regularly remind employees about their responsibilities in maintaining a secure work environment.
- Encourage reporting of suspicious activities: Establish clear channels for reporting suspected fraudulent behavior or security incidents confidentially. Assure employees that their concerns will be taken seriously and investigated appropriately.
- Conduct regular audits: Perform periodic internal audits to assess compliance with established policies and procedures. These audits can help identify any gaps or weaknesses in controls that need attention.
- Implement strong authentication measures: Enforce the use of strong passwords and consider implementing two-factor authentication (2FA) for critical systems. This adds an extra layer of security by requiring users to provide additional verification, such as a unique code sent to their mobile device.
- Respond swiftly to incidents: If fraudulent activity is suspected or detected, respond promptly and decisively. Follow established incident response procedures, involve appropriate stakeholders, and engage legal counsel if necessary.
Remember that preventing employee fraud and malicious activity requires a combination of preventive measures, ongoing monitoring, and a proactive response. By implementing these strategies, you can significantly reduce the risk of internal threats and protect your business from potential harm.
What are the best practices for implementing enterprise security policies?
Implementing effective enterprise security policies is crucial for protecting your organization’s digital assets and mitigating cybersecurity risks. Here are some best practices to consider:
- Conduct a thorough risk assessment: Begin by identifying and assessing potential risks and vulnerabilities within your organization’s infrastructure, systems, and processes. This will help you prioritize areas that require immediate attention and allocate resources accordingly.
- Develop a comprehensive security policy: Create a well-defined security policy that outlines the organization’s expectations, guidelines, and procedures for maintaining a secure environment. Ensure that the policy covers areas such as data protection, access control, incident response, employee responsibilities, and compliance with relevant regulations.
- Establish strong access controls: Implement strict user authentication mechanisms such as strong passwords, two-factor authentication (2FA), or biometric verification to control access to sensitive data and critical systems. Regularly review user privileges to ensure they align with job roles and responsibilities.
- Encrypt sensitive data: Utilize encryption techniques to protect sensitive information both at rest (stored on servers or devices) and in transit (during transmission). Encryption ensures that even if data is compromised, it remains unreadable without the appropriate decryption key.
- Regularly update software and systems: Promptly apply software patches and updates released by vendors to address known vulnerabilities in your systems. Consider implementing an automated patch management system to streamline this process.
- Educate employees on cybersecurity best practices: Conduct regular training sessions to raise awareness about common cyber threats such as phishing attacks, social engineering tactics, and malware infections. Encourage employees to follow good security practices like using strong passwords, avoiding suspicious links or attachments, and reporting any suspicious activities promptly.
- Implement robust network security measures: Deploy firewalls, intrusion detection/prevention systems (IDS/IPS), virtual private networks (VPNs), and other network security solutions to protect against unauthorized access attempts and monitor network traffic for potential threats.
- Monitor system activity and logs: Implement a Security Information and Event Management (SIEM) system to collect and analyze logs from various sources within your network. This enables you to detect anomalies, identify potential security incidents, and respond proactively.
- Regularly backup critical data: Establish a robust data backup strategy that includes regular backups of critical systems and data. Ensure that backups are stored securely off-site or in the cloud to protect against data loss in the event of a breach or system failure.
- Conduct periodic security audits: Regularly assess and audit your security measures to identify any gaps or weaknesses. Engage third-party experts if necessary to conduct thorough penetration testing or vulnerability assessments.
- Stay informed about emerging threats: Keep up-to-date with the latest cybersecurity trends, vulnerabilities, and best practices by following industry news, attending conferences, and participating in relevant forums or communities. This knowledge will help you adapt your security policies as new threats emerge.
Remember that implementing enterprise security policies is an ongoing process. Regularly review and update your policies to address evolving threats and ensure compliance with changing regulations. By following these best practices, you can enhance your organization’s resilience against cyber threats and protect valuable assets effectively.
How can I stay up-to-date with the latest security technologies and trends?
Staying up-to-date with the latest security technologies and trends is crucial in maintaining a strong defense against cyber threats. Here are a few strategies to help you stay informed:
- Follow reputable cybersecurity news sources: Subscribe to trusted cybersecurity news websites, blogs, and newsletters that provide regular updates on the latest security technologies, emerging threats, and industry trends. Some popular sources include SecurityWeek, Dark Reading, KrebsOnSecurity, and Threatpost.
- Engage with professional communities: Join online forums or social media groups dedicated to cybersecurity professionals. Participate in discussions, ask questions, and share knowledge with like-minded individuals who can provide insights into the latest technologies and trends.
- Attend industry conferences and webinars: Attend cybersecurity conferences, seminars, or webinars where experts discuss emerging threats, innovative technologies, and best practices. These events often feature keynote speeches, panel discussions, and workshops that delve into current security issues.
- Join professional associations: Become a member of professional associations or organizations related to cybersecurity such as ISACA (Information Systems Audit and Control Association), ISC(2) (International Information System Security Certification Consortium), or CompTIA Security+. These organizations offer resources like research papers, webinars, training programs, and networking opportunities that can keep you updated on the latest security developments.
- Follow industry thought leaders: Identify influential figures in the cybersecurity field who regularly share their insights through blogs or social media platforms. Follow them to gain valuable perspectives on new technologies and emerging trends.
- Continuous learning: Invest time in continuous learning by pursuing relevant certifications such as Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), or Certified Information Security Manager (CISM). These certifications often require ongoing education to maintain your credentials and keep you up-to-date with the evolving landscape of security technologies.
- Vendor updates: Stay informed about updates from your existing security vendors or technology providers by subscribing to their newsletters or following them on social media. They often release new features, patches, and updates to address emerging threats or enhance their products.
- Engage in threat intelligence sharing: Collaborate with other organizations or industry groups to share threat intelligence and best practices. By participating in information-sharing initiatives, you can gain insights into the latest attack techniques and defensive strategies.
Remember, cybersecurity is a rapidly evolving field, so staying up-to-date requires ongoing effort and a commitment to continuous learning. By actively seeking knowledge from diverse sources and engaging with the cybersecurity community, you can stay ahead of the curve and effectively protect your digital assets.