Title: The Rising Threat of Data Breaches: Safeguarding Your Digital Footprint
Introduction:
Data breaches have become an all too common occurrence in today’s digital landscape, posing significant risks to individuals and organizations alike. With cybercriminals becoming more sophisticated, it is crucial to understand the implications of data breaches and take proactive measures to protect our valuable personal information. In this article, we will delve into the world of data breaches, their impact, and steps you can take to safeguard your digital footprint.
Understanding Data Breaches:
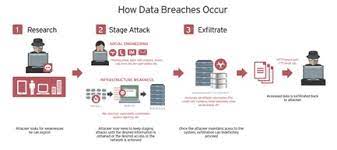
A data breach occurs when unauthorized individuals gain access to sensitive or confidential information. This can include personal details such as names, addresses, social security numbers, financial data, or even trade secrets and intellectual property for businesses. Cybercriminals employ various techniques like hacking, phishing, malware attacks, or exploiting vulnerabilities in systems to breach security defenses.
The Impact of Data Breaches:
The consequences of a data breach can be far-reaching and devastating. For individuals, stolen personal information can lead to identity theft, financial loss, or even reputational damage. Businesses face severe reputational harm as well as legal and financial repercussions due to potential lawsuits and regulatory fines. Moreover, the loss of customer trust can have long-term consequences for any organization.
Protecting Your Digital Footprint:
While it may seem daunting to protect yourself against data breaches in an increasingly interconnected world, there are several practical steps you can take:
- Strong Passwords: Use unique and complex passwords for all your online accounts. Utilize a password manager tool to securely store and manage them.
- Two-Factor Authentication (2FA): Enable 2FA whenever possible as an extra layer of security that requires additional verification beyond passwords.
- Regular Software Updates: Keep your operating system, applications, and antivirus software up-to-date to patch any vulnerabilities that cybercriminals may exploit.
- Be Wary of Phishing Attempts: Be cautious of suspicious emails, messages, or phone calls asking for personal information. Verify the authenticity of the sender before sharing any sensitive data.
- Limit Personal Information Sharing: Be mindful of the information you share online and on social media platforms. Minimize the exposure of personal details that could be used against you.
- Encrypt Sensitive Data: Utilize encryption tools to protect your sensitive files and communications, making it harder for unauthorized individuals to access them.
- Regular Data Backups: Create regular backups of your important files and store them securely offline or in cloud storage with strong encryption.
- Educate Yourself: Stay informed about current cybersecurity threats and best practices to ensure you can respond appropriately to potential risks.
Conclusion:
Data breaches are a growing concern in our digital age, posing significant risks to individuals and organizations alike. By understanding the implications of data breaches and implementing robust security measures, we can safeguard our digital footprints and protect ourselves from potential harm. Remember, being proactive in securing your personal information is key to staying one step ahead of cybercriminals in this ever-evolving landscape.
5 Essential Tips to Protect Your Data from Breaches
- Make sure your systems are up to date with the latest security patches and antivirus software.
- Use strong passwords for all accounts and change them regularly.
- Utilise two-factor authentication where possible for added protection of sensitive data.
- Monitor your systems regularly for any suspicious activity or anomalies, such as unusual logins or data transfers.
- Educate all staff members on how to identify potential threats and what to do in the event of a breach, including reporting it immediately to the relevant authorities or IT teams within your organisation.
Make sure your systems are up to date with the latest security patches and antivirus software.
Title: The Importance of Keeping Your Systems Secure: Updating Security Patches and Antivirus Software
In today’s digital world, where cyber threats are constantly evolving, it is crucial to stay one step ahead by ensuring that your systems are up to date with the latest security patches and antivirus software. This simple yet powerful tip can significantly enhance your defense against data breaches and protect your valuable information from falling into the wrong hands.
Security patches are updates released by software developers to address vulnerabilities in their systems. These vulnerabilities, if left unpatched, can be exploited by cybercriminals to gain unauthorized access to your data. By regularly installing these patches, you close potential entry points for attackers and fortify your system’s security.
Similarly, antivirus software plays a critical role in safeguarding your digital environment. It acts as a shield against malware, ransomware, and other malicious programs that can compromise your sensitive information. Antivirus software scans files and programs for any signs of malicious activity and removes or quarantines them before they can cause harm.
Here are some key reasons why keeping your systems up to date with security patches and antivirus software is vital:
- Protection Against Known Vulnerabilities: Developers release security patches in response to identified vulnerabilities. By promptly installing these updates, you ensure that any known weaknesses in your system are addressed, reducing the risk of exploitation.
- Defense Against Emerging Threats: Cybercriminals continually develop new techniques and exploit undiscovered vulnerabilities. Regularly updating both security patches and antivirus software ensures that you have the latest defenses against these emerging threats.
- Prevention of Exploits: Attackers often target outdated software as it tends to have known vulnerabilities that they can exploit easily. By keeping your systems updated, you minimize the chances of falling victim to such exploits.
- Enhanced Performance: Security patches not only address security issues but also improve system performance by fixing bugs or optimizing processes. Up-to-date antivirus software ensures efficient scanning and detection of threats without causing significant slowdowns.
- Compliance with Regulations: Many industries have specific regulatory requirements for data security. Regularly updating your systems demonstrates your commitment to meeting these standards and helps you avoid potential penalties or legal repercussions.
In conclusion, making sure your systems are up to date with the latest security patches and antivirus software is a fundamental step in protecting yourself against data breaches. By staying vigilant and proactive in maintaining the security of your digital environment, you can safeguard your sensitive information and enjoy a safer online experience. Remember, a small effort today can save you from significant consequences tomorrow.
Use strong passwords for all accounts and change them regularly.
In today’s digital world, where our personal information is increasingly stored online, using strong passwords and regularly changing them is a crucial step in protecting ourselves against data breaches.
A strong password acts as a powerful barrier between our sensitive information and potential cybercriminals. It should be unique, complex, and difficult to guess. Avoid using common passwords like “123456” or “password,” as these are easily cracked by hackers.
To create a strong password, consider the following tips:
- Length: Aim for a password that is at least 12 characters long. The longer the password, the harder it is to crack.
- Complexity: Include a combination of uppercase and lowercase letters, numbers, and special characters in your password. This makes it more difficult for automated programs to guess.
- Avoid Personal Information: Do not use easily guessable information like your name, birthdate, or address in your password. Hackers can easily find this information online.
- Unique Passwords: Use different passwords for each of your accounts. Reusing passwords across multiple accounts increases the risk of a data breach affecting multiple areas of your digital life.
- Regularly Change Passwords: It’s important to update your passwords regularly to ensure ongoing security. Aim to change them every three to six months or immediately after any potential security incident.
Remembering multiple complex passwords can be challenging, but there are tools available such as password managers that securely store and generate unique passwords for each account you have.
By using strong passwords and changing them regularly, you significantly reduce the chances of falling victim to data breaches and unauthorized access to your personal information.
In an ever-evolving digital landscape where cyber threats continue to grow in sophistication, taking this simple yet effective step can go a long way in safeguarding your valuable data and maintaining peace of mind online.
Utilise two-factor authentication where possible for added protection of sensitive data.
In the ever-evolving landscape of cybersecurity, one simple yet effective measure stands out: two-factor authentication (2FA). This additional layer of security provides added protection for your sensitive data, making it harder for cybercriminals to gain unauthorized access. By utilising 2FA wherever possible, you can significantly reduce the risk of falling victim to data breaches.
Two-factor authentication works by requiring users to provide two separate forms of identification before accessing an account or system. Typically, this involves something you know (like a password) and something you have (like a unique code sent to your mobile device). This combination ensures that even if your password gets compromised, the hacker would still need physical possession of your second factor to gain access.
The benefits of 2FA are clear. Firstly, it adds an extra layer of security beyond just a password. Even if someone manages to obtain or guess your password, they would still require the second factor to proceed. This significantly reduces the chances of unauthorized access.
Secondly, 2FA provides peace of mind by offering real-time alerts and notifications whenever someone tries to log in using your credentials. If you receive an unexpected verification code or login attempt alert, it could be a sign that someone is trying to breach your account. With this information at hand, you can take immediate action and change passwords or notify the relevant authorities.
Implementing 2FA is relatively straightforward as many online platforms and services offer it as an option. Common methods include SMS verification codes, authenticator apps like Google Authenticator or Microsoft Authenticator, or even biometric factors like fingerprints or facial recognition.
While two-factor authentication provides an additional layer of security, it is important to remember that no security measure is foolproof. It should be used in conjunction with other best practices such as strong passwords and regular software updates.
In conclusion, leveraging two-factor authentication where possible is a wise decision when it comes to protecting sensitive data. By adding this extra layer of security, you significantly reduce the risk of falling victim to data breaches and unauthorized access. Take the proactive step towards safeguarding your digital accounts and enjoy the peace of mind that comes with knowing your information is better protected.
Monitor your systems regularly for any suspicious activity or anomalies, such as unusual logins or data transfers.
Title: Stay Vigilant: Monitoring Systems to Detect Data Breaches
In today’s digital world, where data breaches have become a prevalent threat, it is essential to adopt proactive measures to protect our sensitive information. One crucial step in safeguarding against data breaches is regularly monitoring our systems for any signs of suspicious activity or anomalies. By staying vigilant and promptly detecting potential breaches, we can mitigate the risks and minimize the impact.
Monitoring for Suspicious Activity:
Monitoring your systems involves actively observing and analyzing various indicators that may suggest unauthorized access or data compromise. Here are some key aspects to consider:
Unusual Logins: Keep a close eye on login activities within your systems. Look out for login attempts from unfamiliar IP addresses or devices, as well as multiple failed login attempts indicating potential brute-force attacks.
Data Transfers: Monitor any unusual or unexpected data transfers, particularly large volumes of data being sent outside your network or to unknown locations. This could indicate unauthorized access or exfiltration of sensitive information.
Irregular User Behavior: Pay attention to user behavior patterns within your systems. Identify any abnormal actions, such as privileged users accessing unauthorized areas or performing actions beyond their usual scope of work.
System Performance: Keep track of system performance metrics regularly. Sudden drops in performance or unusual network traffic patterns may indicate the presence of malware or malicious activities compromising your system’s integrity.
Security Logs and Alerts: Enable and review security logs and alerts provided by your operating system, applications, and security tools. These logs often contain valuable information about potential security incidents that require investigation.
Taking Action:
Once you detect any suspicious activity or anomalies during system monitoring, it is crucial to take immediate action:
Investigate: Thoroughly investigate the identified incident by analyzing relevant logs, conducting forensic analysis if necessary, and determining the extent of the breach.
Contain: Isolate affected systems or accounts to prevent further damage or unauthorized access. This may involve temporarily disabling compromised accounts or disconnecting affected devices from the network.
Mitigate: Implement necessary security measures to mitigate the impact of the breach. This may include patching vulnerabilities, updating security configurations, or enhancing access controls.
Notify Authorities: Depending on the severity and nature of the breach, consider reporting the incident to relevant authorities, such as law enforcement agencies or data protection regulators.
Conclusion:
Regularly monitoring your systems for suspicious activity is a crucial aspect of protecting against data breaches. By promptly detecting and responding to potential breaches, you can minimize the impact on your sensitive information and maintain a robust security posture. Remember, staying vigilant and proactive in monitoring your systems is an essential step towards safeguarding your digital assets in today’s ever-evolving threat landscape.
Educate all staff members on how to identify potential threats and what to do in the event of a breach, including reporting it immediately to the relevant authorities or IT teams within your organisation.
Title: Strengthening Your Defense: Educating Staff to Combat Data Breaches
In the battle against data breaches, one of the most effective weapons at your disposal is a well-informed and vigilant workforce. Educating all staff members on how to identify potential threats and respond appropriately in the event of a breach is crucial in maintaining the security of your organization’s valuable data. Let’s explore why this tip is essential and how it can fortify your defense against cyber threats.
Identifying Potential Threats:
Cybercriminals are constantly evolving their tactics, making it imperative for employees at all levels to be able to recognize potential threats. By educating staff members on common phishing techniques, social engineering scams, suspicious emails, or unusual website requests, you empower them to become the first line of defense. Encourage employees to be cautious and skeptical when interacting with unfamiliar or unexpected digital communications.
Immediate Reporting:
Time is of the essence when dealing with data breaches. Encourage a culture of immediate reporting within your organization, ensuring that staff members understand the importance of promptly notifying relevant authorities or IT teams about any suspicious activity or potential breach. This swift response allows for quicker containment measures to be implemented, minimizing the impact and potential damage caused by a breach.
Collaboration with Authorities and IT Teams:
Educate your staff on the proper channels for reporting data breaches within your organization. Ensure they are aware of whom they should contact in case of an incident, whether it’s internal IT teams or designated authorities responsible for handling cybersecurity matters. Establish clear protocols and provide training sessions that outline step-by-step procedures for reporting incidents effectively.
Ongoing Training and Awareness:
Data breach prevention is an ongoing effort that requires continuous education and awareness among staff members. Regularly conduct training sessions or workshops focused on emerging threats, best practices for data security, and any updates to internal policies or procedures. Encourage open communication channels where employees can report suspicious activities without fear of retribution, fostering a collaborative and proactive security culture.
The Benefits of Educating Staff:
By investing in staff education, you create a workforce that is not only more resilient against cyber threats but also more engaged and accountable for data security. Empowering employees with knowledge and the ability to identify potential threats allows them to play an active role in safeguarding sensitive information. This collective effort strengthens your organization’s overall cybersecurity posture and reduces the likelihood of successful data breaches.
Conclusion:
In the fight against data breaches, educating all staff members on how to identify potential threats and respond effectively is a critical step towards fortifying your organization’s defenses. By fostering a culture of vigilance, immediate reporting, and collaboration with authorities or IT teams, you empower your workforce to become proactive guardians of data security. Remember, an educated staff is an invaluable asset in the ongoing battle against cyber threats.