The Ultimate Guide to L2TP IPsec VPN
Layer 2 Tunneling Protocol (L2TP) with Internet Protocol Security (IPsec) is a popular VPN protocol that provides a secure and encrypted connection for remote access to private networks. It combines the best features of both protocols to offer a robust and reliable VPN solution.
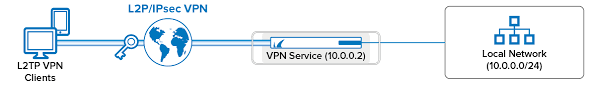
L2TP establishes a tunnel between the user’s device and the VPN server, while IPsec encrypts the data passing through the tunnel, ensuring confidentiality and integrity. This double-layered security approach makes L2TP IPsec VPN ideal for protecting sensitive information and maintaining privacy online.
One of the key advantages of L2TP IPsec VPN is its compatibility with a wide range of devices and operating systems, including Windows, macOS, iOS, Android, and Linux. This versatility makes it a popular choice for businesses and individuals looking to secure their internet connections across multiple platforms.
Setting up an L2TP IPsec VPN is relatively straightforward, with most operating systems offering built-in support for the protocol. Users can configure their devices to connect to a remote server using L2TP IPsec settings provided by their VPN service provider.
When using L2TP IPsec VPN, users can enjoy enhanced security features such as data encryption, authentication, and data integrity verification. This ensures that sensitive information remains protected from prying eyes and potential cyber threats while browsing the internet or accessing private network resources.
In conclusion, L2TP IPsec VPN is a reliable and secure protocol that offers robust protection for users seeking privacy and security online. Its ease of use, broad compatibility, and strong encryption make it an excellent choice for individuals and businesses looking to safeguard their digital communications.
Understanding L2TP IPsec VPN: Key FAQs Answered
- What is L2TP IPsec VPN?
- How does L2TP IPsec VPN work?
- What are the advantages of using L2TP IPsec VPN?
- Is L2TP IPsec VPN secure?
- How do I set up L2TP IPsec VPN on my device?
- Which operating systems support L2TP IPsec VPN?
- Can I use L2TP IPsec VPN for accessing geo-restricted content?
What is L2TP IPsec VPN?
L2TP IPsec VPN, short for Layer 2 Tunneling Protocol with Internet Protocol Security, is a secure and reliable VPN protocol that creates a protected tunnel between a user’s device and a VPN server. This tunnel encrypts the data passing through it, ensuring confidentiality and integrity of the information transmitted. L2TP IPsec VPN is favoured for its dual-layered security approach, making it an ideal choice for individuals and businesses looking to safeguard their online activities and sensitive data from potential cyber threats. Its compatibility with various devices and operating systems further enhances its appeal as a trusted solution for establishing secure connections to private networks.
How does L2TP IPsec VPN work?
Layer 2 Tunneling Protocol (L2TP) with Internet Protocol Security (IPsec) VPN works by creating a secure tunnel between the user’s device and the VPN server. L2TP establishes the tunnel, while IPsec provides encryption and authentication for the data passing through it. This combined approach ensures that all communication between the user and the server is encrypted, protecting it from potential eavesdropping or tampering. By using L2TP IPsec VPN, users can securely access private networks or browse the internet while maintaining confidentiality and data integrity.
What are the advantages of using L2TP IPsec VPN?
There are several advantages to using L2TP IPsec VPN. Firstly, it provides a high level of security by encrypting data transmitted between the user’s device and the VPN server, ensuring that sensitive information remains confidential and secure. Secondly, L2TP IPsec VPN is widely supported across various devices and operating systems, making it a versatile choice for users who require secure connections on multiple platforms. Additionally, the protocol offers strong authentication mechanisms and data integrity verification, further enhancing the overall security of the VPN connection. Overall, L2TP IPsec VPN is a reliable and effective solution for users looking to protect their online privacy and maintain a secure connection to private networks.
Is L2TP IPsec VPN secure?
When it comes to the security of L2TP IPsec VPN, users can rest assured that it offers a high level of security for their online activities. The combination of Layer 2 Tunneling Protocol (L2TP) and Internet Protocol Security (IPsec) creates a robust encryption mechanism that ensures data confidentiality and integrity. With strong encryption algorithms and authentication methods in place, L2TP IPsec VPN is considered a secure protocol for establishing private and encrypted connections over the internet. Users can trust in the protection provided by L2TP IPsec VPN to safeguard their sensitive information and maintain privacy while browsing online or accessing remote networks.
How do I set up L2TP IPsec VPN on my device?
Setting up L2TP IPsec VPN on your device is a straightforward process that typically involves accessing the VPN settings on your device and entering the required configuration details provided by your VPN service provider. First, navigate to the VPN settings menu on your device and select the option to add a new VPN connection. Choose L2TP IPsec as the protocol type and enter the server address, username, password, pre-shared key, and any other necessary information provided by your VPN provider. Once you have entered all the required details, save the settings and connect to the VPN server. Your device should now be securely connected to the L2TP IPsec VPN, ensuring that your online activities are encrypted and protected from potential security threats.
Which operating systems support L2TP IPsec VPN?
Various operating systems support L2TP IPsec VPN, making it a versatile choice for users across different platforms. Commonly used operating systems such as Windows, macOS, iOS, Android, and Linux all have built-in support for L2TP IPsec VPN. This broad compatibility allows users to secure their internet connections and access private networks using L2TP IPsec VPN on a wide range of devices, ensuring that privacy and security are maintained regardless of the operating system being used.
Can I use L2TP IPsec VPN for accessing geo-restricted content?
Yes, you can use L2TP IPsec VPN for accessing geo-restricted content. By connecting to a VPN server in a different location, you can mask your real IP address and appear as if you are browsing from that specific region. This allows you to bypass geo-restrictions imposed by websites or streaming services and access content that may be otherwise unavailable in your location. L2TP IPsec VPN provides a secure and encrypted connection while also offering the added benefit of accessing geo-blocked content, making it a versatile solution for both privacy and content accessibility online.