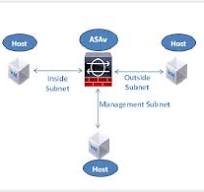
The Power of Cisco ASAv in Modern Cybersecurity
In the realm of cybersecurity, where threats evolve at an alarming pace, having robust network security solutions is paramount. Cisco Adaptive Security Virtual Appliance (ASAv) stands out as a powerful tool in defending against cyber attacks and safeguarding critical data.
ASAv is a virtualized security appliance that offers the same features and capabilities as Cisco’s physical security appliances but in a software form. This flexibility allows organisations to deploy and scale their security measures more efficiently, without the need for additional hardware.
One of the key strengths of ASAv is its versatility. It can be deployed in various environments, including on-premises data centres, private clouds, public clouds, and hybrid cloud environments. This adaptability makes ASAv an ideal choice for businesses with diverse IT infrastructures.
ASAv provides comprehensive threat protection through features such as firewalling, VPN capabilities, intrusion prevention systems (IPS), and advanced malware protection. Its ability to inspect traffic at multiple layers of the OSI model ensures that malicious activities are detected and blocked effectively.
Moreover, ASAv integrates seamlessly with other Cisco security solutions, creating a unified defence system that enhances visibility and control across the network. This interconnected ecosystem enables organisations to respond swiftly to emerging threats and enforce consistent security policies.
As cyber threats become more sophisticated and pervasive, organisations need agile and resilient cybersecurity solutions. Cisco ASAv empowers businesses to fortify their networks against evolving threats while maintaining operational efficiency and scalability.
Top 6 Advantages of Cisco ASAv: Versatile, Comprehensive, and Scalable Security Solutions
- 1. Versatile deployment options in various environments.
- 2. Offers the same features as physical security appliances but in a virtualized form.
- 3. Comprehensive threat protection with firewalling, VPN capabilities, IPS, and advanced malware protection.
- 4. Scalable security solution without the need for additional hardware.
- 5. Seamless integration with other Cisco security products for enhanced network defence.
- 6. Enables swift response to emerging threats and consistent enforcement of security policies.
Six Drawbacks of Cisco ASAv: Resource Intensity, Cost, and More
- 1. Resource Intensive
- 2. Cost
- 3. Complexity
- 4. Performance Limitations
- 5. Licensing Fees
- 6. Support Dependency
1. Versatile deployment options in various environments.
Cisco ASAv offers versatile deployment options in various environments, making it a highly adaptable solution for modern cybersecurity needs. Whether deployed in on-premises data centres, private clouds, public clouds, or hybrid cloud environments, ASAv seamlessly integrates into different infrastructures. This flexibility not only simplifies the deployment process but also ensures that organisations can maintain consistent security measures across diverse IT landscapes. By providing such versatile deployment options, Cisco ASAv empowers businesses to enhance their security posture effectively and efficiently in any environment they operate in.
2. Offers the same features as physical security appliances but in a virtualized form.
Cisco ASAv offers the significant advantage of providing all the features and functionalities of traditional physical security appliances but in a virtualized form. This innovation allows organisations to enjoy the same level of security capabilities without the constraints of physical hardware, leading to increased flexibility, scalability, and cost-effectiveness in implementing and managing their network security infrastructure.
3. Comprehensive threat protection with firewalling, VPN capabilities, IPS, and advanced malware protection.
Cisco ASAv offers comprehensive threat protection by integrating essential security features such as firewalling, VPN capabilities, intrusion prevention systems (IPS), and advanced malware protection. This multi-layered approach ensures that organisations can effectively defend against a wide range of cyber threats, from unauthorized access attempts to sophisticated malware attacks. By combining these critical security functions into a single virtual appliance, ASAv provides a holistic solution that strengthens network security and minimises vulnerabilities, ultimately enhancing the overall cybersecurity posture of businesses.
4. Scalable security solution without the need for additional hardware.
One of the standout advantages of Cisco ASAv is its scalability as a security solution without requiring additional hardware. This feature allows organisations to expand their security measures efficiently and cost-effectively, adapting to changing needs without the logistical challenges of procuring and installing new physical appliances. By leveraging ASAv’s virtualized architecture, businesses can easily scale their security infrastructure to meet growing demands, ensuring comprehensive protection across their network without the constraints of traditional hardware limitations.
5. Seamless integration with other Cisco security products for enhanced network defence.
One significant advantage of Cisco ASAv is its seamless integration with other Cisco security products, which enhances network defence capabilities. By working in harmony with a range of complementary security solutions from Cisco, ASAv creates a unified and interconnected defence system that boosts visibility and control across the network. This integrated approach allows organisations to respond swiftly to emerging threats, enforce consistent security policies, and fortify their overall cybersecurity posture effectively.
6. Enables swift response to emerging threats and consistent enforcement of security policies.
Cisco ASAv offers a significant advantage by enabling organisations to respond quickly to emerging threats and maintain consistent enforcement of security policies. By providing real-time threat detection and response capabilities, ASAv ensures that any potential security breaches are identified and addressed promptly. This proactive approach allows businesses to stay ahead of cyber threats and minimise the impact of attacks. Additionally, the seamless integration with other Cisco security solutions ensures that security policies are enforced consistently across the network, enhancing overall protection and reducing vulnerabilities.
1. Resource Intensive
One notable drawback of Cisco ASAv is its resource-intensive nature, demanding substantial CPU and memory resources to function optimally. This can pose challenges for organisations with limited hardware capabilities or those operating in resource-constrained environments. The high resource requirements of ASAv may lead to performance issues, increased operational costs, and potential scalability limitations, making it crucial for users to carefully assess their infrastructure capacity before deploying this security solution.
2. Cost
One notable drawback of implementing Cisco ASAv is the cost factor. While ASAv offers robust security features and scalability, it may require a higher upfront investment compared to other virtual security appliances. This initial cost consideration could be a limiting factor for organisations with budget constraints or those seeking more cost-effective solutions in the short term. However, it’s essential to weigh this upfront expense against the long-term benefits and comprehensive security capabilities that Cisco ASAv brings to the table.
3. Complexity
The complexity of configuring and managing Cisco ASAv can pose a significant challenge, particularly for users who do not possess extensive networking expertise. The intricate setup process and the technical knowledge required to optimally manage ASAv may deter some users from fully utilising its capabilities. This complexity can lead to potential errors in configuration, which could compromise the effectiveness of the security measures put in place. Organizations considering the adoption of Cisco ASAv should be prepared to invest time and resources in training their staff or seek external support to navigate through the intricacies of this powerful but intricate security solution.
4. Performance Limitations
In high-traffic environments, one notable drawback of Cisco ASAv is its potential performance limitations, which could hinder network throughput. The processing demands of handling heavy traffic volumes may strain the capabilities of ASAv, leading to reduced performance levels that could affect the overall efficiency and responsiveness of the network. It is essential for organisations operating in such environments to carefully assess the scalability and performance requirements of ASAv to ensure that it can effectively meet their needs without compromising network operations.
5. Licensing Fees
One notable drawback of Cisco ASAv is the potential for additional licensing fees to be incurred for certain features or functionalities within the ecosystem. These extra costs can impact the overall budget of organisations deploying ASAv, especially if they require access to specific advanced capabilities. The necessity to pay additional licensing fees for certain functionalities may lead to unexpected expenses and could potentially limit the accessibility of key security features for some users. Careful consideration and planning are essential to ensure that organisations understand and account for these licensing fees when adopting Cisco ASAv as part of their cybersecurity strategy.
6. Support Dependency
One notable drawback of Cisco ASAv is the support dependency it entails. The effective deployment and maintenance of this virtual security appliance often necessitate continuous assistance from specialised IT personnel or external consultants. This reliance on skilled professionals can lead to increased operational costs and potential delays in addressing security issues, especially for organisations with limited resources or expertise in managing complex cybersecurity solutions.