The Importance of Defender for Endpoint Vulnerability Management
In today’s digital landscape, cybersecurity threats are constantly evolving and becoming more sophisticated. It is crucial for organisations to have robust security measures in place to protect their sensitive data and systems. One key aspect of a comprehensive cybersecurity strategy is vulnerability management, and Microsoft Defender for Endpoint offers powerful tools to help organisations effectively manage vulnerabilities.
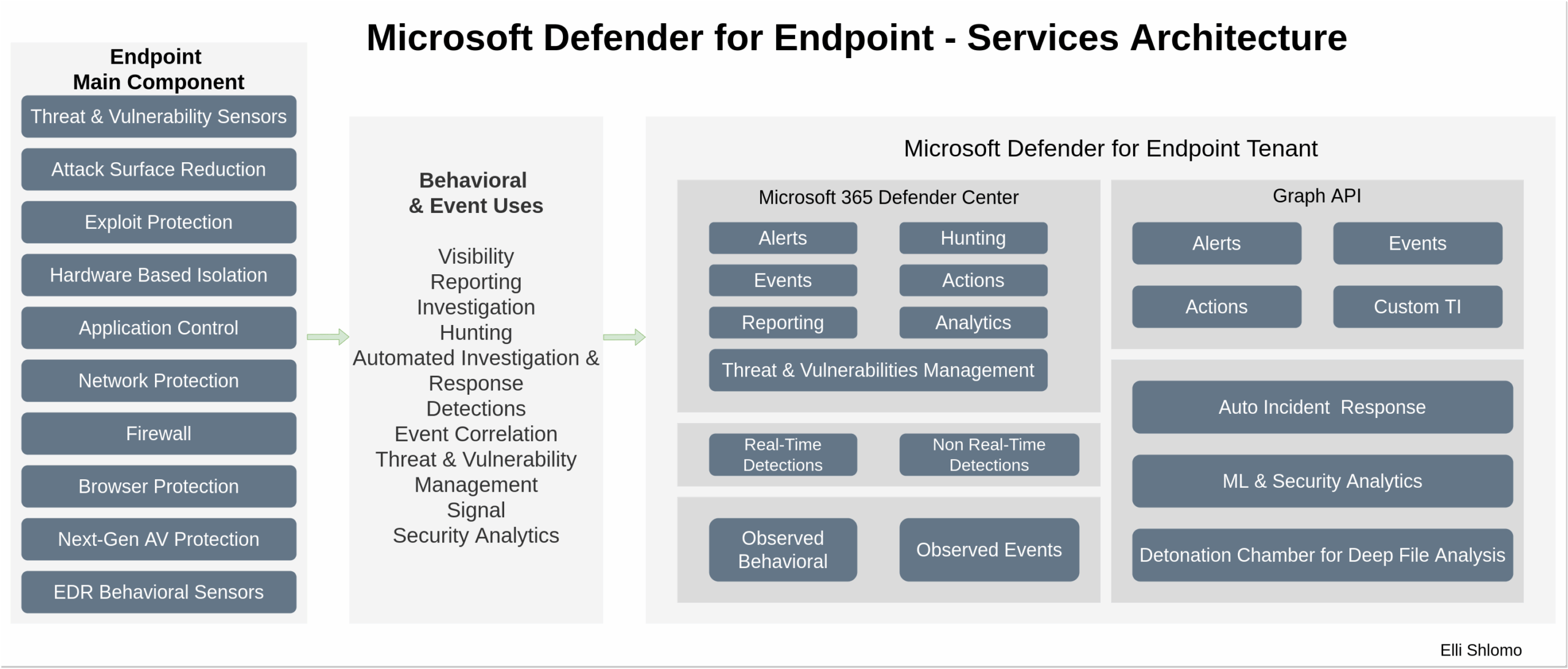
What is Defender for Endpoint?
Microsoft Defender for Endpoint is a comprehensive endpoint security solution that provides advanced threat protection, post-breach detection, automated investigation, and response capabilities. One of its key features is vulnerability management, which helps organisations identify and remediate security weaknesses in their systems before they can be exploited by cyber attackers.
The Benefits of Vulnerability Management with Defender for Endpoint
By using Defender for Endpoint’s vulnerability management capabilities, organisations can:
- Identify vulnerabilities across all endpoints in the network
- Prioritise vulnerabilities based on their severity and potential impact
- Automate the patching process to quickly remediate vulnerabilities
- Monitor the effectiveness of patching efforts and track progress over time
- Gain insights into common attack vectors and trends to proactively strengthen defences
Conclusion
In conclusion, effective vulnerability management is essential for maintaining a strong security posture in the face of ever-evolving cyber threats. Microsoft Defender for Endpoint provides organisations with the tools they need to identify, prioritise, and remediate vulnerabilities across their endpoints efficiently. By leveraging these capabilities, organisations can better protect their data, systems, and users from malicious actors.
Top 5 Tips for Enhancing Endpoint Security and Vulnerability Management
- Regularly update the endpoint protection software to patch vulnerabilities.
- Implement strong access controls to prevent unauthorised access to endpoints.
- Enable real-time monitoring and alerts for suspicious activities on endpoints.
- Utilise endpoint encryption to protect sensitive data stored on devices.
- Conduct regular vulnerability assessments and penetration testing on endpoints.
Regularly update the endpoint protection software to patch vulnerabilities.
To enhance the effectiveness of Defender for Endpoint vulnerability management, it is crucial to adhere to the best practice of regularly updating the endpoint protection software to patch vulnerabilities. By staying current with software updates, organisations can ensure that any identified security weaknesses are promptly addressed, reducing the risk of exploitation by cyber threats. This proactive approach not only strengthens the overall security posture but also helps in maintaining a robust defence mechanism against evolving threats in today’s digital landscape.
Implement strong access controls to prevent unauthorised access to endpoints.
Implementing strong access controls is a crucial tip in Microsoft Defender for Endpoint vulnerability management. By enforcing strict access policies, organisations can effectively prevent unauthorised users from accessing sensitive endpoints, reducing the risk of security breaches and data compromise. Strong access controls help ensure that only authorised individuals can interact with critical systems, enhancing overall cybersecurity resilience and safeguarding valuable assets from potential threats.
Enable real-time monitoring and alerts for suspicious activities on endpoints.
Enabling real-time monitoring and alerts for suspicious activities on endpoints is a crucial tip when utilising Defender for Endpoint vulnerability management. By setting up this feature, organisations can proactively detect and respond to potential security breaches as they occur, allowing them to swiftly mitigate risks and limit the impact of cyber threats. Real-time monitoring provides visibility into endpoint activities, enabling security teams to identify unusual behaviour or signs of compromise promptly. By staying vigilant and responsive to alerts, organisations can enhance their overall cybersecurity posture and safeguard their systems against malicious attacks effectively.
Utilise endpoint encryption to protect sensitive data stored on devices.
To enhance the security of sensitive data stored on devices, a valuable tip within Defender for Endpoint vulnerability management is to utilise endpoint encryption. By implementing endpoint encryption, organisations can safeguard their critical information from unauthorised access or data breaches. This proactive measure ensures that even if a device is compromised, the encrypted data remains protected, mitigating the risk of potential data leaks and maintaining a higher level of security across endpoints.
Conduct regular vulnerability assessments and penetration testing on endpoints.
To enhance the security of your endpoints using Defender for Endpoint vulnerability management, it is crucial to conduct regular vulnerability assessments and penetration testing. By regularly assessing vulnerabilities and conducting penetration tests on endpoints, you can proactively identify potential weaknesses in your systems before they are exploited by cyber threats. This proactive approach allows you to address security gaps promptly, strengthen your defences, and mitigate the risk of security breaches. Regular assessments and testing play a vital role in maintaining a robust cybersecurity posture and ensuring the protection of your sensitive data and systems.