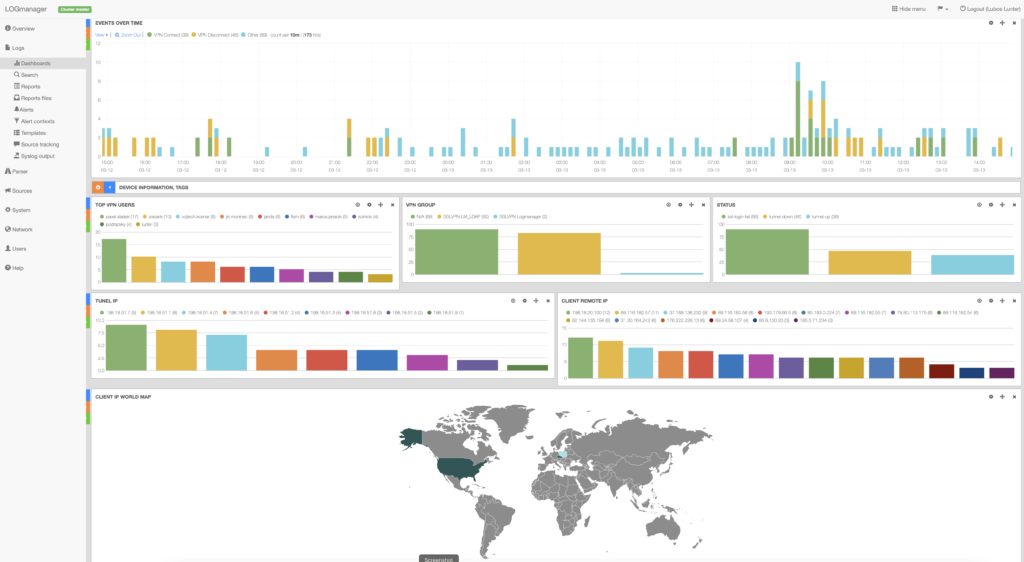
Understanding the Importance of Security Log Management
In today’s digital landscape, where cyber threats are becoming increasingly sophisticated and prevalent, security log management plays a crucial role in safeguarding sensitive information and maintaining the integrity of systems. Security log management involves the collection, monitoring, analysis, and retention of logs generated by various devices and applications within an organisation’s network.
By effectively managing security logs, organisations can gain valuable insights into potential security incidents, track user activity, detect anomalies, and respond promptly to any suspicious behaviour. Security logs serve as a valuable source of information for identifying security breaches, investigating incidents, and ensuring regulatory compliance.
Key benefits of security log management include:
- Early Detection: By monitoring security logs in real-time, organisations can detect unusual patterns or activities that may indicate a security threat before it escalates.
- Forensic Analysis: Security logs provide a detailed record of events that can be invaluable in conducting forensic investigations following a security incident.
- Compliance: Many regulatory standards require organisations to maintain and review security logs regularly to demonstrate compliance with data protection regulations.
- Incident Response: Security log management enables organisations to quickly identify and respond to security incidents, minimising the impact on operations.
To effectively manage security logs, organisations should implement robust log collection mechanisms, employ automated tools for log analysis, establish clear logging policies and procedures, and ensure secure storage of log data. Regular monitoring and review of security logs are essential to maintaining a proactive cybersecurity posture.
In conclusion, security log management is an integral component of any comprehensive cybersecurity strategy. By investing in effective log management practices, organisations can enhance their ability to detect and respond to threats promptly, mitigate risks, and protect their valuable assets from cyber attacks.
Understanding Security Log Management: Key Questions and Insights for Effective Implementation
- What is security log management and why is it important?
- How does security log management help in detecting security incidents?
- What are the key benefits of implementing a security log management system?
- What are the best practices for collecting and analysing security logs?
- How can organisations ensure the confidentiality and integrity of their security logs?
- What role does compliance play in security log management?
What is security log management and why is it important?
Security log management is the process of collecting, monitoring, analysing, and retaining logs generated by various devices and applications within an organisation’s network to enhance cybersecurity. It plays a vital role in identifying security incidents, tracking user activity, detecting anomalies, and ensuring regulatory compliance. Security log management is important because it enables organisations to proactively detect potential security threats, respond promptly to suspicious activities, conduct forensic investigations following incidents, demonstrate compliance with data protection regulations, and minimise the impact of security breaches on operations. By implementing effective security log management practices, organisations can strengthen their defences against cyber threats and safeguard their sensitive information from malicious actors.
How does security log management help in detecting security incidents?
Security log management plays a crucial role in detecting security incidents by providing organisations with a comprehensive record of activities within their network. By monitoring and analysing security logs in real-time, organisations can identify unusual patterns, suspicious activities, or potential security breaches. Security logs capture valuable information such as login attempts, file access, system changes, and network traffic, which can be analysed to detect anomalies or indicators of compromise. Timely detection of security incidents through effective log management allows organisations to respond promptly, investigate the root cause of the incident, and implement necessary remediation measures to prevent further damage or data loss.
What are the key benefits of implementing a security log management system?
Implementing a security log management system offers a range of key benefits for organisations seeking to enhance their cybersecurity posture. One of the primary advantages is the early detection of security incidents through real-time monitoring of logs, enabling prompt responses to potential threats before they escalate. Additionally, security log management facilitates forensic analysis by providing a detailed record of events, aiding in investigations following security breaches. Compliance with regulatory standards is also simplified as organisations can demonstrate adherence to data protection regulations through regular review and maintenance of security logs. Furthermore, having a robust security log management system in place enables efficient incident response, allowing organisations to identify and address security issues swiftly to minimise operational disruptions and safeguard critical assets.
What are the best practices for collecting and analysing security logs?
When it comes to collecting and analysing security logs, adhering to best practices is essential for maintaining a robust cybersecurity posture. Firstly, organisations should ensure that all relevant devices and applications are configured to generate comprehensive logs that capture relevant security events. It is crucial to centralise log collection from various sources to facilitate efficient analysis and correlation of data. Implementing automated tools for log analysis can help in identifying anomalies and potential security incidents in real-time. Regularly reviewing and monitoring security logs, setting up alerts for suspicious activities, and establishing clear logging policies are also key best practices. Additionally, organisations should securely store log data to preserve its integrity for forensic analysis and compliance purposes. By following these best practices, organisations can enhance their ability to detect and respond to security threats effectively.
How can organisations ensure the confidentiality and integrity of their security logs?
Organisations can ensure the confidentiality and integrity of their security logs by implementing robust security measures and best practices. To maintain confidentiality, organisations should restrict access to security logs to authorised personnel only, using role-based access controls and encryption techniques to safeguard sensitive information. Regularly reviewing and auditing access logs can help detect any unauthorised attempts to view or modify log data. Ensuring the integrity of security logs involves implementing secure logging mechanisms, such as digital signatures or checksums, to detect any tampering or manipulation of log entries. Additionally, storing log data in secure, tamper-evident repositories and regularly backing up logs to prevent data loss are essential steps in preserving the integrity of security logs. By following these measures diligently, organisations can uphold the confidentiality and integrity of their security logs effectively.
What role does compliance play in security log management?
Compliance plays a significant role in security log management by setting standards and guidelines that organisations must adhere to in order to protect sensitive data and maintain the integrity of their systems. Many regulatory frameworks, such as GDPR, HIPAA, and PCI DSS, require organisations to implement robust security log management practices to ensure the confidentiality, integrity, and availability of data. Compliance regulations often mandate the collection, monitoring, analysis, and retention of security logs as part of demonstrating adherence to industry-specific security requirements. By aligning with compliance standards, organisations can enhance their cybersecurity posture, mitigate risks, and demonstrate their commitment to safeguarding data privacy and security.