Zscaler VPN: Enhancing Security and Connectivity
In today’s digital landscape, the need for secure and reliable connectivity is paramount. Zscaler VPN stands out as a leading solution that offers both enhanced security and seamless access to resources.
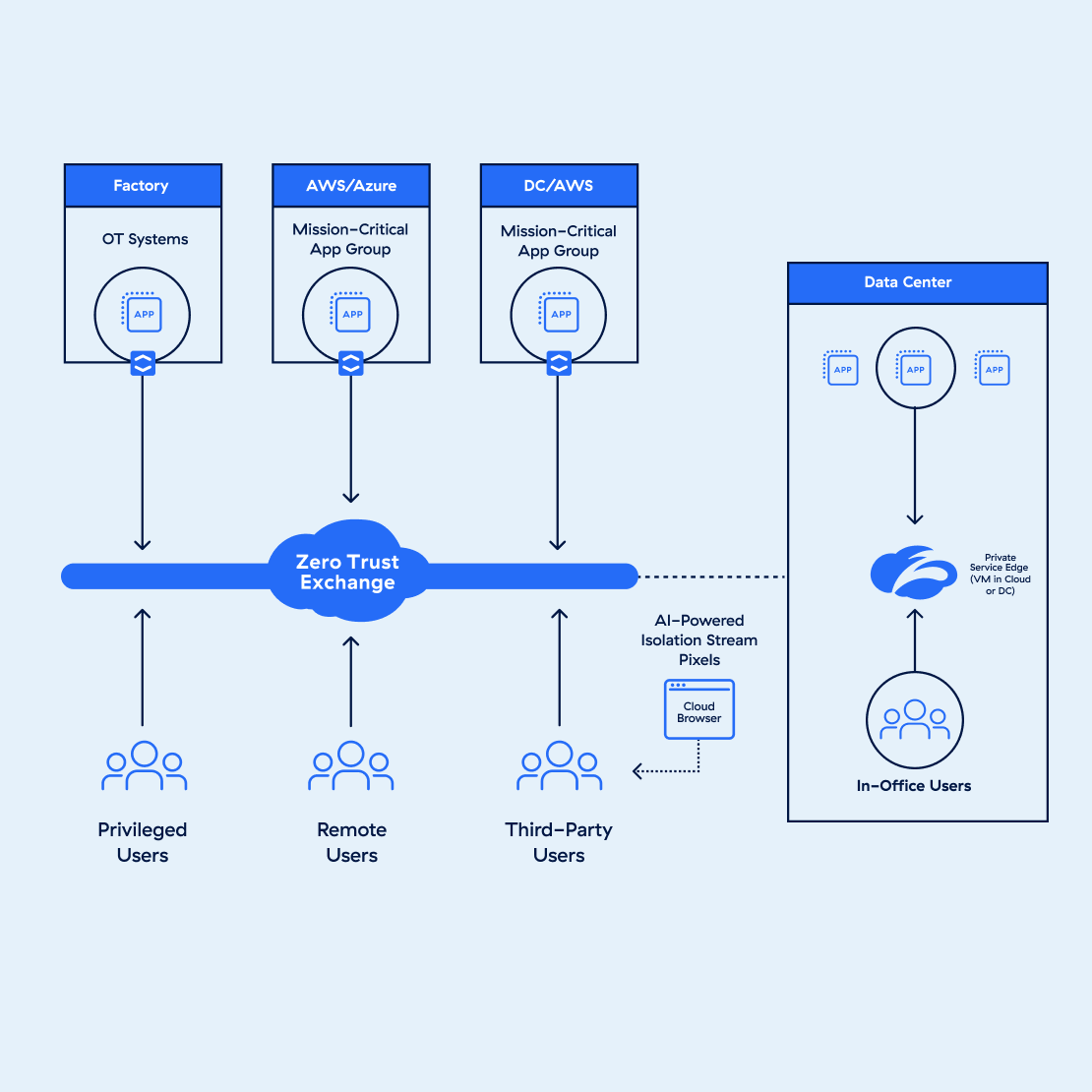
Unlike traditional VPNs, Zscaler VPN operates in the cloud, providing a more agile and scalable approach to remote access. This cloud-native design ensures that users can connect to the network securely from any location without compromising performance.
One of the key advantages of Zscaler VPN is its robust security features. By routing traffic through Zscaler’s cloud platform, users benefit from advanced threat protection, data encryption, and access control mechanisms. This helps safeguard sensitive information and mitigate cyber risks effectively.
Moreover, Zscaler VPN offers a user-friendly experience with intuitive interfaces and seamless integration across devices. Whether employees are working from home, on the go, or in the office, they can easily connect to the network without sacrificing productivity or security.
Organisations that adopt Zscaler VPN gain not only enhanced security but also improved network performance and reduced complexity. By consolidating networking and security functions in the cloud, Zscaler VPN streamlines operations and ensures a consistent user experience across various environments.
In conclusion, Zscaler VPN is a powerful tool for organisations looking to bolster their security posture while enabling secure connectivity for remote workers. With its cloud-based architecture, advanced security features, and user-friendly interface, Zscaler VPN sets a new standard for modern remote access solutions.
Top 9 Frequently Asked Questions About Zscaler VPN: Features, Setup, and Performance
- What is Zscaler VPN?
- How does Zscaler VPN work?
- Is Zscaler VPN easy to set up?
- Yes, Zscaler VPN offers a user-friendly setup process with intuitive interfaces for seamless deployment across devices.
- What security features does Zscaler VPN offer?
- Can I use Zscaler VPN on multiple devices?
- Does Zscaler VPN impact network performance?
- Is customer support available for Zscaler VPN users?
- Can I integrate Zscaler VPN with existing security solutions?
What is Zscaler VPN?
Zscaler VPN is a cloud-based virtual private network (VPN) solution that offers secure and seamless connectivity for users accessing corporate resources remotely. Unlike traditional VPNs, Zscaler VPN operates in the cloud, providing advanced security features such as threat protection, data encryption, and access control. This innovative approach ensures that users can securely connect to the network from any location without compromising performance or user experience. Zscaler VPN is designed to simplify remote access while enhancing security measures, making it an ideal solution for organisations looking to protect their data and ensure secure connectivity for their employees.
How does Zscaler VPN work?
Zscaler VPN operates by leveraging a cloud-based architecture to provide secure and seamless remote access to network resources. When a user initiates a connection through Zscaler VPN, their traffic is encrypted and routed through Zscaler’s global cloud platform. This process ensures that data remains protected from potential threats while in transit. By utilising advanced security protocols and access control mechanisms, Zscaler VPN verifies the user’s identity and grants them secure access to authorised resources. This cloud-native approach not only enhances security but also optimises performance by reducing latency and enabling users to connect from any location with ease.
Is Zscaler VPN easy to set up?
Setting up Zscaler VPN is a straightforward process that does not require advanced technical expertise. Zscaler provides user-friendly guides and resources to assist users in configuring the VPN client on their devices efficiently. With clear instructions and intuitive interfaces, setting up Zscaler VPN can be done quickly and seamlessly, ensuring that users can establish secure connections without unnecessary complications.
Yes, Zscaler VPN offers a user-friendly setup process with intuitive interfaces for seamless deployment across devices.
Certainly! Here’s a paragraph about the frequently asked question regarding Zscaler VPN:
“Yes, Zscaler VPN indeed provides a user-friendly setup process, featuring intuitive interfaces that ensure seamless deployment across various devices. Whether you are a novice user or an IT professional, the straightforward configuration steps and user-friendly interface of Zscaler VPN make it easy to set up and deploy the solution across your devices. This simplicity not only saves time but also enhances the overall user experience, making secure remote access more accessible and efficient for all users.”
What security features does Zscaler VPN offer?
Zscaler VPN offers a comprehensive range of security features to ensure robust protection for users accessing the network remotely. These include advanced threat protection mechanisms, data encryption protocols, and access control measures. By routing traffic through Zscaler’s cloud platform, the VPN effectively shields sensitive information from potential cyber threats. Additionally, Zscaler VPN’s security features are designed to safeguard user privacy and prevent unauthorised access to corporate resources, providing peace of mind for organisations seeking a secure and reliable remote access solution.
Can I use Zscaler VPN on multiple devices?
Yes, Zscaler VPN allows users to utilise the service on multiple devices for added convenience and flexibility. Whether you are working from your laptop, accessing resources on your smartphone, or connecting from a tablet, Zscaler VPN supports seamless connectivity across various devices. This feature ensures that users can stay productive and securely access the network from any location without limitations. With Zscaler VPN’s multi-device support, you can enjoy consistent protection and reliable access to resources across all your devices.
Does Zscaler VPN impact network performance?
When considering the impact of Zscaler VPN on network performance, it’s essential to highlight the cloud-native architecture of Zscaler VPN, which is designed to optimise connectivity without compromising speed or reliability. By routing traffic through Zscaler’s cloud platform, the VPN minimises latency and ensures efficient data transmission. Additionally, Zscaler VPN’s advanced traffic optimisation techniques help streamline network traffic, resulting in improved performance for users accessing resources remotely. Overall, Zscaler VPN is engineered to enhance network performance while providing robust security measures, making it a valuable asset for organisations prioritising both speed and protection in their remote access solutions.
Is customer support available for Zscaler VPN users?
For Zscaler VPN users, customer support is readily available to address any queries or issues that may arise during the setup or usage of the VPN service. The dedicated customer support team at Zscaler is committed to providing timely assistance and guidance to ensure a seamless experience for users. Whether it’s troubleshooting technical issues, clarifying configuration settings, or seeking general assistance, Zscaler VPN users can rely on the knowledgeable support staff to help resolve their concerns effectively.
Can I integrate Zscaler VPN with existing security solutions?
Integrating Zscaler VPN with existing security solutions is a common concern for many organisations seeking to maintain a cohesive and comprehensive security infrastructure. Fortunately, Zscaler VPN is designed to support seamless integration with a wide range of security tools and platforms. By leveraging APIs and custom configurations, organisations can synchronise Zscaler VPN with their existing security solutions to create a unified defence strategy. This interoperability not only enhances the overall security posture but also streamlines management processes, enabling organisations to benefit from the strengths of both Zscaler VPN and their current security ecosystem.