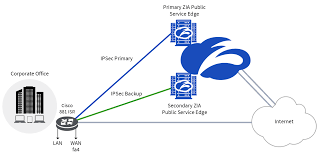
IPSec VPN Service: Secure Your Online Connections
In today’s digital age, ensuring the security and privacy of your online activities is more important than ever. One effective way to achieve this is through an IPSec VPN service.
IPSec, which stands for Internet Protocol Security, is a protocol suite that encrypts and authenticates data transferred over IP networks. When you use an IPSec VPN service, your internet traffic is encrypted, making it virtually impossible for hackers, ISPs, or other third parties to intercept or monitor your online communications.
By using an IPSec VPN service, you can:
- Secure your sensitive data when accessing public Wi-Fi networks
- Bypass geo-restrictions and access region-locked content
- Mask your IP address and maintain anonymity online
Setting up an IPSec VPN service is straightforward and typically involves installing a client application on your device. Once connected to the VPN server, all your internet traffic is routed through a secure tunnel, ensuring end-to-end encryption.
It’s important to choose a reputable IPSec VPN service provider that prioritises user privacy and data security. Look for providers that offer strong encryption protocols, a strict no-logs policy, and servers in multiple locations for optimal performance.
Whether you’re concerned about cyber threats, want to protect your online privacy, or simply need to access restricted content securely, an IPSec VPN service can be a valuable tool in safeguarding your digital presence.
Take control of your online security today with an IPSec VPN service and enjoy peace of mind knowing that your internet activities are shielded from prying eyes.
Six Essential Tips for Securing Your IPsec VPN Service
- Ensure strong authentication methods are used, such as certificates or two-factor authentication.
- Regularly update and patch VPN software to protect against known vulnerabilities.
- Implement proper access controls to restrict VPN usage to authorised users only.
- Encrypt all data transmitted over the IPsec VPN to ensure confidentiality.
- Monitor VPN traffic for any unusual activity that may indicate a security breach.
- Establish clear policies and procedures for secure usage of the IPsec VPN service.
Ensure strong authentication methods are used, such as certificates or two-factor authentication.
When utilising an IPSec VPN service, it is crucial to prioritise security by ensuring that robust authentication methods are in place. Strong authentication measures, such as the use of certificates or two-factor authentication, add an extra layer of protection to your online connections. By implementing these methods, you can significantly enhance the security of your VPN connection and safeguard your sensitive data from unauthorized access. It is essential to choose an IPSec VPN service provider that offers advanced authentication options to fortify your digital defences effectively.
Regularly update and patch VPN software to protect against known vulnerabilities.
Regularly updating and patching your IPSec VPN software is crucial to safeguarding your online security. By staying on top of software updates, you ensure that any known vulnerabilities are promptly addressed, reducing the risk of potential cyber threats compromising your VPN connection. Keeping your IPSec VPN software up to date not only enhances its performance but also strengthens its resilience against emerging security risks, providing you with a more secure and reliable online experience.
Implement proper access controls to restrict VPN usage to authorised users only.
Implementing proper access controls is crucial when utilising an IPSec VPN service to ensure that only authorised users have access. By restricting VPN usage to authenticated individuals, you can significantly enhance the security of your network and data. This measure helps prevent unauthorised access and strengthens the overall integrity of your VPN connection, providing peace of mind knowing that only trusted users are able to benefit from the secure communication channel established by the IPSec VPN service.
Encrypt all data transmitted over the IPsec VPN to ensure confidentiality.
To enhance the security of your online activities when using an IPSec VPN service, it is crucial to encrypt all data transmitted over the network. By encrypting your data, you ensure that sensitive information remains confidential and protected from potential eavesdroppers or cyber threats. This extra layer of security provided by encryption adds a robust shield to your online communications, reinforcing the confidentiality of your data as it travels through the secure IPSec VPN tunnel.
Monitor VPN traffic for any unusual activity that may indicate a security breach.
It is crucial to monitor your IPSec VPN traffic for any unusual activity that could signal a security breach. By keeping a close eye on the data flowing through your VPN connection, you can quickly detect any anomalies or suspicious behaviour that may indicate unauthorized access or malicious activity. Regularly reviewing your VPN traffic logs and being vigilant for any deviations from the norm can help you proactively identify and respond to potential security threats, ensuring the integrity of your online communications and data privacy.
Establish clear policies and procedures for secure usage of the IPsec VPN service.
To ensure the effective and secure usage of an IPSec VPN service, it is crucial to establish clear policies and procedures governing its usage. By defining guidelines on how the service should be accessed, used, and maintained, organisations can mitigate potential risks and ensure that all users adhere to best practices in cybersecurity. These policies should outline protocols for user authentication, data encryption standards, device compliance requirements, and incident response procedures to uphold the integrity and security of the IPSec VPN service. By implementing robust policies and procedures, organisations can enhance their overall cybersecurity posture and safeguard sensitive information transmitted over the VPN network.