The Power of Encryption in Securing Your Data
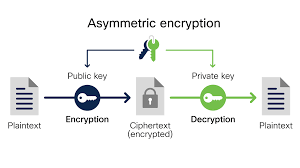
Encryption is a powerful tool that plays a crucial role in safeguarding sensitive information in today’s digital age. It involves the process of encoding data so that only authorized parties can access it, effectively protecting it from unauthorized access or interception.
One of the key benefits of encryption is its ability to ensure confidentiality. By encrypting your data, you can prevent prying eyes from viewing or stealing sensitive information such as personal details, financial records, or business secrets. This is particularly important when transmitting data over the internet, where cyber threats abound.
Moreover, encryption also helps maintain the integrity of your data. By using cryptographic algorithms to encode information, any unauthorized modifications or tampering attempts can be detected, ensuring that the data remains accurate and trustworthy.
Additionally, encryption enhances data security by providing authentication mechanisms. Through techniques like digital signatures and certificates, encryption allows users to verify the identity of the sender and ensure that the received data has not been altered during transit.
End-to-end encryption has become increasingly prevalent in modern communication technologies such as messaging apps and email services. This ensures that only the sender and intended recipient can access the content of their communications, shielding it from potential eavesdroppers or hackers.
As cyber threats continue to evolve and become more sophisticated, encryption remains a fundamental tool in protecting sensitive information from falling into the wrong hands. By incorporating encryption into your digital practices, you can significantly enhance the security and privacy of your data.
Remember, when it comes to safeguarding your digital assets, encryption is a powerful ally that you should not overlook.
Seven Essential Tips for Robust Data Encryption Security
- Use strong and unique passwords for encryption keys.
- Regularly update encryption software to protect against vulnerabilities.
- Encrypt sensitive data both at rest and in transit.
- Implement two-factor authentication for an added layer of security.
- Be cautious of phishing attacks that could compromise encryption keys.
- Backup encrypted data regularly to prevent data loss.
- Consider using end-to-end encryption for secure communication.
Use strong and unique passwords for encryption keys.
When it comes to encryption, a crucial tip to enhance security is to use strong and unique passwords for encryption keys. Encryption keys act as the gateway to unlock and access encrypted data, making them a prime target for cyber attackers. By using complex and unique passwords for encryption keys, you can significantly bolster the protection of your sensitive information. Strong passwords that combine a mix of letters, numbers, and special characters make it harder for hackers to crack the encryption and gain unauthorized access to your data. Remember, the strength of your encryption is only as robust as the security measures you implement to safeguard your encryption keys.
Regularly update encryption software to protect against vulnerabilities.
Regularly updating your encryption software is essential in maintaining robust protection against potential vulnerabilities. By staying up-to-date with the latest security patches and enhancements, you can fortify your data against emerging threats and ensure that your encryption algorithms remain resilient to cyber attacks. Keeping your encryption software current not only safeguards your sensitive information but also reinforces the overall security posture of your digital environment. Stay proactive in updating your encryption tools to stay one step ahead of malicious actors and safeguard the confidentiality and integrity of your data effectively.
Encrypt sensitive data both at rest and in transit.
To enhance the security of sensitive data, it is essential to encrypt it both at rest and in transit. Encrypting data at rest ensures that information stored on devices or servers remains protected from unauthorized access, even if the physical storage is compromised. Similarly, encrypting data in transit secures information as it travels between devices or over networks, shielding it from interception by cybercriminals. By implementing encryption measures at every stage of data handling, organisations can significantly reduce the risk of data breaches and safeguard the confidentiality and integrity of their valuable information.
Implement two-factor authentication for an added layer of security.
Implementing two-factor authentication is a highly effective tip for enhancing security through encryption. By requiring users to provide two forms of identification before accessing their accounts, such as a password and a unique code sent to their mobile device, this additional layer of security significantly reduces the risk of unauthorised access. Two-factor authentication strengthens encryption measures by adding an extra barrier that cybercriminals would need to overcome, making it a valuable tool in safeguarding sensitive information and bolstering overall data protection efforts.
Be cautious of phishing attacks that could compromise encryption keys.
It is crucial to remain vigilant against phishing attacks that pose a threat to the security of encryption keys. Phishing attempts often target individuals with deceptive emails or messages, aiming to trick them into revealing sensitive information such as passwords or encryption keys. By compromising these keys, attackers can gain unauthorized access to encrypted data, undermining the protection that encryption provides. Therefore, exercising caution and implementing robust security measures are essential in safeguarding encryption keys from malicious actors seeking to exploit vulnerabilities through phishing tactics.
Backup encrypted data regularly to prevent data loss.
Backing up encrypted data regularly is a crucial step in preventing data loss and ensuring the security of your information. By creating backups of your encrypted data, you not only safeguard it from potential threats such as hardware failures or cyber attacks but also ensure that you have a reliable copy available in case of emergencies. Regular backups provide an added layer of protection, giving you peace of mind knowing that your encrypted data is securely stored and easily recoverable when needed.
Consider using end-to-end encryption for secure communication.
When it comes to ensuring the utmost security in your communication, considering the use of end-to-end encryption is paramount. This advanced encryption method guarantees that only the sender and intended recipient can access the content of their messages or data, providing a high level of confidentiality and protection against potential eavesdroppers or cyber threats. By implementing end-to-end encryption, you can communicate with peace of mind, knowing that your sensitive information remains secure throughout its journey.