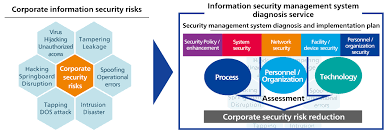
Information Security Management: Safeguarding the Digital World
In today’s interconnected world, where information flows freely and technology drives every aspect of our lives, the need for robust information security management has never been more critical. With cyber threats becoming increasingly sophisticated and prevalent, organizations and individuals must take proactive measures to protect their sensitive data and ensure the integrity of their digital systems.
Information security management refers to the systematic approach of identifying, assessing, and mitigating risks to safeguard valuable information assets. It encompasses a range of practices, policies, and technologies designed to maintain the confidentiality, integrity, and availability of data.
One of the key components of effective information security management is risk assessment. Organizations must identify potential vulnerabilities and threats to their systems and evaluate the potential impact they could have on their operations. This enables them to prioritize their security efforts and allocate resources accordingly.
Implementing robust security controls is another crucial aspect of information security management. These controls can include firewalls, encryption protocols, access controls, intrusion detection systems, and regular software updates. By implementing these measures, organizations can significantly reduce the risk of unauthorized access or data breaches.
However, information security management is not solely dependent on technology. It also requires a comprehensive understanding of human behavior within an organization. Employees must be educated about best practices in information security and trained to recognize potential threats such as phishing attempts or social engineering attacks. Regular training programs can help create a culture of vigilance where everyone understands their role in protecting sensitive information.
Furthermore, compliance with relevant laws and regulations is essential for effective information security management. Organizations must stay up-to-date with legal requirements regarding data protection and privacy to ensure they are operating within the boundaries set by legislation such as the General Data Protection Regulation (GDPR) in Europe or the California Consumer Privacy Act (CCPA) in the United States.
Continuous monitoring and evaluation are vital components of any successful information security management program. Regular audits allow organizations to assess the effectiveness of their security measures, identify any weaknesses or gaps, and make necessary improvements. Additionally, staying informed about emerging threats and new security technologies is crucial to adapt to the ever-evolving landscape of cyber risks.
In conclusion, information security management is an essential discipline that helps protect our digital world from malicious actors and potential data breaches. By implementing comprehensive risk assessment processes, robust security controls, employee education programs, and compliance with relevant regulations, organizations can significantly enhance their ability to safeguard sensitive information. In an era where data is a valuable asset, investing in information security management is not only a necessity but also a fundamental responsibility in ensuring the trust and confidence of customers and stakeholders alike.
Commonly Asked Questions about Information Security Management
- What are the five main principles of information security management?
- What do you mean by security information management?
- What are the 7 P’s of information security management?
- What is role in information security management?
What are the five main principles of information security management?
The five main principles of information security management are:
- Confidentiality: This principle ensures that sensitive information is only accessible to authorized individuals or entities. It involves protecting data from unauthorized access, disclosure, or modification. Measures such as encryption, access controls, and secure storage help maintain confidentiality.
- Integrity: The integrity principle focuses on maintaining the accuracy and completeness of data throughout its lifecycle. It involves preventing unauthorized modifications or tampering with data. Techniques like data validation, checksums, and digital signatures can be used to ensure data integrity.
- Availability: This principle ensures that information and systems are accessible and usable when needed. It involves implementing measures to prevent disruptions or outages that could impact availability, such as redundancy, backup systems, disaster recovery plans, and robust network infrastructure.
- Authenticity: Authenticity refers to verifying the identity of users or entities accessing information or systems. It involves implementing authentication mechanisms like passwords, biometrics, or multi-factor authentication to ensure that only authorized individuals can access sensitive resources.
- Non-repudiation: Non-repudiation ensures that the originator of a message cannot later deny their involvement in sending it. It provides evidence of the integrity and authenticity of communication transactions through techniques like digital signatures or timestamping.
These principles form the foundation of information security management practices and guide organizations in designing comprehensive security strategies to protect their valuable assets from various threats and risks in today’s digital landscape.
What do you mean by security information management?
Apologies for any confusion caused. “Security Information Management” (SIM) is a term used to describe the process of collecting, analyzing, and managing security-related data within an organization. It involves the use of specialized software tools and systems to aggregate data from various sources, such as network devices, servers, firewalls, intrusion detection systems, and other security devices.
The primary purpose of Security Information Management is to provide organizations with a centralized platform for monitoring and analyzing security events and incidents. By consolidating data from multiple sources into a single interface or system, SIM enables security analysts to have a holistic view of the organization’s security posture.
The key functions of Security Information Management include:
- Log Collection: SIM solutions collect logs and security event data from various sources across the network infrastructure. This can include firewall logs, antivirus logs, system logs, and more.
- Event Correlation: SIM tools analyze collected data to identify patterns or relationships between different events. By correlating events across multiple devices or systems, potential threats or suspicious activities can be detected.
- Alerting and Notification: When specific predefined conditions or thresholds are met, SIM systems generate alerts or notifications to inform security personnel about potential security incidents that require attention.
- Incident Response: Security Information Management provides a framework for incident response by facilitating the investigation and analysis of security incidents. It helps in identifying the root cause of incidents and aids in formulating appropriate remediation measures.
- Reporting and Compliance: SIM solutions generate reports that provide insights into an organization’s overall security posture. These reports can be used for compliance purposes (e.g., demonstrating adherence to regulatory requirements) as well as for ongoing risk management and decision-making processes.
Overall, Security Information Management plays a crucial role in enhancing an organization’s ability to detect, respond to, and mitigate potential security threats effectively. By providing real-time visibility into security events across the enterprise infrastructure, it enables proactive monitoring, incident response, and continuous improvement of the organization’s security posture.
What are the 7 P’s of information security management?
The 7 P’s of Information Security Management refer to a framework that helps organizations establish and maintain effective security practices. These elements provide a comprehensive approach to managing information security risks. Here are the 7 P’s:
- Policy: Information security policies serve as the foundation for an organization’s security framework. They define the objectives, principles, and guidelines for protecting sensitive information and outline the responsibilities of employees in maintaining security.
- Procedures: Procedures are step-by-step instructions that guide employees on how to implement security measures effectively. They provide clear guidelines on activities such as access control, incident response, data backup, and recovery.
- People: People play a crucial role in information security management. It involves hiring qualified professionals, providing training and awareness programs to educate employees about best practices, promoting a culture of security consciousness, and ensuring that everyone understands their roles and responsibilities in protecting sensitive information.
- Partnerships: Collaboration with external partners is essential in managing information security effectively. Organizations should establish strong relationships with vendors, suppliers, contractors, or other third-party entities to ensure that they adhere to similar security standards when handling sensitive data.
- Processes: Effective processes help streamline information security management activities. This includes risk assessments, incident response procedures, change management processes, vulnerability management processes, and regular audits to identify areas of improvement.
- Products: The selection and implementation of appropriate security products are vital for protecting sensitive information effectively. This includes firewalls, antivirus software, intrusion detection systems (IDS), encryption tools, access control mechanisms, and other technologies that align with an organization’s specific needs.
- Performance Measurement: Regular monitoring and evaluation of the effectiveness of information security controls is crucial for continuous improvement. Metrics such as incident response timeframes, successful vulnerability remediation rates, or employee training completion rates can help identify areas where enhancements are needed.
By considering these 7 P’s in their information security management strategy, organizations can establish a comprehensive framework that addresses the various aspects of protecting sensitive information and mitigating risks effectively.
What is role in information security management?
The role of information security management is to establish and maintain a secure environment for the protection of sensitive information. It involves developing and implementing strategies, policies, procedures, and controls to mitigate risks and safeguard valuable data assets.
Here are some key roles and responsibilities within information security management:
- Risk Assessment: Conducting regular risk assessments to identify potential vulnerabilities and threats to the organization’s information systems. This involves evaluating the likelihood and potential impact of risks, prioritizing them, and developing appropriate mitigation strategies.
- Security Policy Development: Creating comprehensive security policies that outline guidelines, procedures, and best practices for protecting sensitive data. These policies should address areas such as access control, password management, incident response, data classification, and acceptable use of technology resources.
- Security Controls Implementation: Deploying technical controls such as firewalls, intrusion detection systems (IDS), encryption protocols, access controls, antivirus software, and other security measures to prevent unauthorized access or data breaches. These controls should be regularly updated to address emerging threats.
- Compliance Management: Ensuring compliance with relevant laws, regulations, industry standards (such as ISO 27001), contractual obligations (e.g., service level agreements), and internal policies related to information security. This may involve conducting audits or assessments to verify adherence to these requirements.
- Employee Education and Awareness: Developing training programs to educate employees about information security best practices. This includes raising awareness about social engineering attacks (e.g., phishing), promoting strong password hygiene, teaching safe browsing habits, and fostering a culture of security-conscious behavior among staff members.
- Incident Response Planning: Establishing incident response plans that outline the steps to be taken in the event of a security incident or breach. This includes defining roles and responsibilities within the incident response team, establishing communication channels with relevant stakeholders (both internal and external), conducting post-incident analysis for continuous improvement.
- Security Monitoring and Evaluation: Continuously monitoring and evaluating the effectiveness of security controls, policies, and procedures to identify any weaknesses or gaps. This may involve conducting regular security audits, vulnerability assessments, penetration testing, and analyzing security logs for suspicious activities.
- Security Awareness and Communication: Regularly communicating with stakeholders, such as employees, management, and customers, to keep them informed about the organization’s security initiatives, updates, and potential risks. This helps maintain a shared understanding of the importance of information security and encourages a collaborative approach towards protecting sensitive data.
Overall, the role of information security management is to ensure that an organization’s information assets are protected from unauthorized access, disclosure, alteration, or destruction. It requires a proactive and holistic approach that addresses technical, procedural, and human aspects of security to maintain confidentiality, integrity, and availability of information in today’s ever-evolving threat landscape.