The Rise of Intune Zero Trust: A Paradigm Shift in Cybersecurity
In today’s rapidly evolving digital landscape, the traditional security perimeter is no longer sufficient to protect organisations from sophisticated cyber threats. As a result, the concept of Zero Trust has gained traction as a more effective approach to cybersecurity. Microsoft’s Intune Zero Trust is at the forefront of this paradigm shift, offering a comprehensive solution to safeguard data and devices in an increasingly interconnected world.
What is Intune Zero Trust?
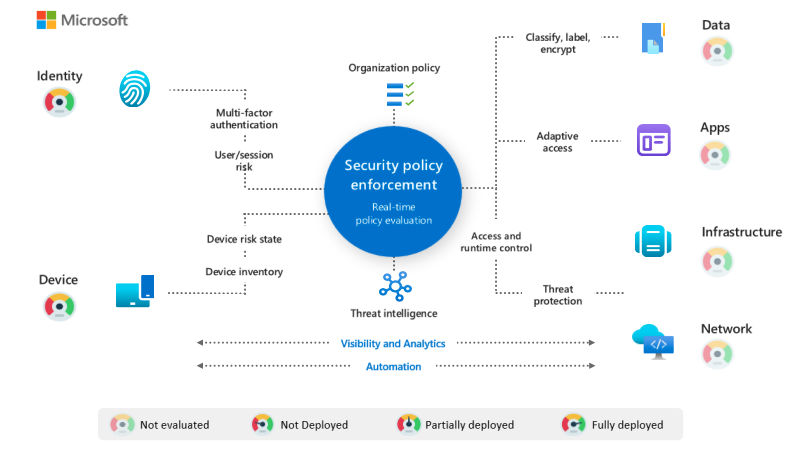
Intune Zero Trust is a security model that assumes no entity, whether inside or outside the network, can be trusted by default. Instead of relying on traditional perimeter-based security measures, such as firewalls and VPNs, Intune Zero Trust focuses on verifying identity and ensuring secure access to resources based on strict policies.
The Core Principles of Intune Zero Trust
At the heart of Intune Zero Trust are three core principles:
- Verify Identity: Users and devices must authenticate their identity before accessing resources.
- Least Privilege Access: Access rights are granted based on the principle of least privilege, ensuring that users only have access to what they need to perform their tasks.
- Continuous Monitoring: Ongoing monitoring and analysis of user behaviour and device health help detect and respond to potential security threats in real-time.
The Benefits of Implementing Intune Zero Trust
By adopting Intune Zero Trust, organisations can enjoy several key benefits:
- Enhanced Security: By eliminating trust assumptions, organisations can reduce the risk of data breaches and unauthorised access.
- Better User Experience: With seamless authentication processes and adaptive access controls, users can enjoy a secure yet frictionless experience.
- Compliance Readiness: Intune Zero Trust helps organisations meet regulatory requirements by enforcing strict access controls and monitoring mechanisms.
In Conclusion
The rise of Intune Zero Trust represents a fundamental shift in how organisations approach cybersecurity. By embracing a model that prioritises identity verification, least privilege access, and continuous monitoring, businesses can better protect their sensitive data and assets in an increasingly complex threat landscape. As cyber threats continue to evolve, implementing solutions like Intune Zero Trust is essential for staying ahead of malicious actors and safeguarding critical resources.
9 Essential Tips for Implementing Zero Trust with Intune
- Implement multi-factor authentication for all users to enhance security.
- Ensure devices are compliant with organisational policies before granting access.
- Utilise conditional access policies to enforce zero trust principles effectively.
- Regularly update and patch all devices to protect against vulnerabilities.
- Monitor user behaviour and device health continuously for anomalies.
- Leverage identity protection features to detect and respond to risks promptly.
- Segment network access based on user roles and requirements.
- Educate employees about the importance of security best practices regularly.
- Conduct regular audits of your zero trust environment for compliance.
Implement multi-factor authentication for all users to enhance security.
Implementing multi-factor authentication for all users is a crucial step in enhancing security within the Intune Zero Trust framework. By requiring users to provide multiple forms of verification before accessing resources, such as a password and a unique code sent to their mobile device, organisations can significantly reduce the risk of unauthorised access and data breaches. Multi-factor authentication adds an extra layer of protection to user accounts, making it more challenging for malicious actors to compromise sensitive information. This proactive measure aligns with the core principle of verifying identity in the Intune Zero Trust model, reinforcing the importance of robust security practices in today’s threat landscape.
Ensure devices are compliant with organisational policies before granting access.
In the realm of Intune Zero Trust, a crucial tip to uphold security is to verify that devices adhere to organisational policies before permitting access. By ensuring that devices meet predefined compliance standards, such as having up-to-date software patches and encryption settings, organisations can mitigate the risk of potential security breaches. This proactive approach not only strengthens the overall security posture but also reinforces the principle of least privilege access, ultimately safeguarding sensitive data and resources from unauthorised users.
Utilise conditional access policies to enforce zero trust principles effectively.
To maximise the effectiveness of Intune Zero Trust, it is essential to leverage conditional access policies. By utilising these policies, organisations can enforce the core principles of zero trust more effectively. Conditional access allows for granular control over access to resources based on specific conditions, such as user identity, device health, and location. This approach ensures that only authorised users with compliant devices can access sensitive data and applications, thereby strengthening security posture and reducing the risk of unauthorised access. Incorporating conditional access policies into an Intune Zero Trust strategy enhances overall cybersecurity defences and helps organisations stay ahead of evolving threats in today’s digital landscape.
Regularly update and patch all devices to protect against vulnerabilities.
Regularly updating and patching all devices is a crucial tip when implementing Intune Zero Trust. By staying on top of software updates, organisations can effectively protect their devices against known vulnerabilities that cyber attackers often exploit. Keeping devices up-to-date ensures that security patches are applied promptly, reducing the risk of potential breaches and strengthening the overall security posture of the network. Embracing a proactive approach to device maintenance is essential in maintaining a secure environment in line with the principles of Intune Zero Trust.
Monitor user behaviour and device health continuously for anomalies.
To enhance the effectiveness of Intune Zero Trust, it is crucial to continuously monitor user behaviour and device health for any anomalies. By implementing real-time monitoring mechanisms, organisations can swiftly detect any suspicious activities or deviations from normal patterns. This proactive approach allows for timely intervention in case of potential security threats, ensuring a higher level of protection for sensitive data and resources. Regular monitoring of user behaviour and device health is essential in maintaining a robust security posture in the dynamic landscape of cybersecurity.
Leverage identity protection features to detect and respond to risks promptly.
To enhance the security of your digital environment with Intune Zero Trust, it is crucial to leverage the identity protection features effectively. By utilising these features, you can detect and respond to potential risks promptly. Identity protection helps in verifying the authenticity of users and devices accessing resources, enabling you to proactively monitor for any suspicious activities or anomalies. By staying vigilant and acting swiftly on any identified risks, you can strengthen your overall security posture and mitigate potential threats effectively.
Segment network access based on user roles and requirements.
In the realm of Intune Zero Trust, a crucial tip is to segment network access according to user roles and specific requirements. By implementing this practice, organisations can enhance their security posture by ensuring that users only have access to the resources necessary for their roles. This approach not only minimises the risk of unauthorised access but also streamlines security management by applying the principle of least privilege. By tailoring network access based on user responsibilities and needs, businesses can effectively bolster their defences against potential cyber threats and safeguard critical assets in an increasingly interconnected digital environment.
Educate employees about the importance of security best practices regularly.
To enhance the effectiveness of Intune Zero Trust, it is crucial to regularly educate employees about the significance of security best practices. By fostering a culture of awareness and vigilance, organisations can empower their workforce to recognise potential threats and adhere to secure protocols. Continuous education on cybersecurity not only reinforces the importance of safeguarding sensitive data but also helps employees understand their role in maintaining a secure digital environment. Through regular training sessions and communication, employees can become proactive contributors to the overall security posture of the organisation, aligning with the principles of Intune Zero Trust to uphold a robust defence against evolving cyber risks.
Conduct regular audits of your zero trust environment for compliance.
It is essential to conduct regular audits of your Intune Zero Trust environment to ensure compliance with security policies and regulations. By regularly reviewing and assessing your security measures, you can identify any potential vulnerabilities or gaps in your zero trust framework. These audits help to verify that access controls are appropriately configured, user identities are authenticated correctly, and devices meet security standards. By proactively monitoring and auditing your zero trust environment, you can strengthen your overall security posture and mitigate the risk of cyber threats.