Network Security Appliances: Safeguarding Your Digital Infrastructure
In today’s interconnected world, where businesses rely heavily on digital networks, ensuring the security of your network infrastructure is paramount. Cyber threats are becoming increasingly sophisticated, making it essential to have robust measures in place to protect your sensitive data and prevent unauthorized access. This is where network security appliances play a crucial role.
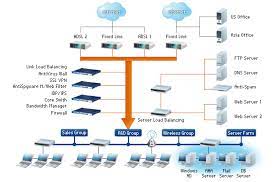
Network security appliances are hardware devices designed to monitor and protect computer networks from various cyber threats, such as malware, viruses, ransomware, and unauthorized access attempts. They act as a first line of defence by inspecting incoming and outgoing network traffic, identifying potential threats, and taking appropriate action to mitigate risks.
One of the key benefits of network security appliances is their ability to provide comprehensive protection across multiple layers of the network. These appliances often incorporate features such as firewalls, intrusion detection/prevention systems (IDS/IPS), virtual private network (VPN) gateways, antivirus/anti-malware scanners, content filtering mechanisms, and more. By combining these functionalities into a single device, businesses can simplify their security infrastructure while ensuring holistic protection.
Firewalls are an integral component of network security appliances. They act as gatekeepers by monitoring incoming and outgoing traffic based on predetermined rules. Firewalls can block suspicious or malicious traffic while allowing legitimate data packets to pass through. This helps prevent unauthorized access attempts and safeguards against potential breaches.
Intrusion detection/prevention systems (IDS/IPS) are another critical feature found in many network security appliances. These systems monitor network traffic for signs of suspicious activities or known attack patterns. If any suspicious activity is detected, IDS/IPS can take immediate action by alerting administrators or automatically blocking the source IP address to prevent further intrusion attempts.
Virtual private network (VPN) gateways are essential for secure remote access to corporate networks. Network security appliances with built-in VPN capabilities ensure that remote employees or branch offices can securely connect to the main network, encrypting data transmission and protecting sensitive information from interception.
Antivirus/anti-malware scanners are designed to detect and eliminate malicious software from network traffic. These scanners continuously monitor data packets for known malware signatures or suspicious behavior, preventing malware from infiltrating the network and compromising devices or data.
Content filtering mechanisms are also commonly included in network security appliances. They allow businesses to enforce policies regarding web browsing, blocking access to potentially harmful or inappropriate websites. Content filtering helps prevent employees from visiting malicious websites that could introduce threats into the network.
Network security appliances offer several advantages over individual software-based security solutions. By consolidating multiple security functions into a single device, they simplify management and reduce complexity. Moreover, hardware-based appliances often provide better performance and scalability compared to software-only solutions.
When choosing a network security appliance, it is crucial to consider factors such as the size of your network, the level of protection required, ease of management, scalability options, and compatibility with existing infrastructure. Consulting with cybersecurity experts can help you select the most suitable appliance for your specific needs.
In conclusion, network security appliances are indispensable tools for safeguarding your digital infrastructure against ever-evolving cyber threats. By providing comprehensive protection across multiple layers of the network, these devices help businesses maintain secure and resilient networks. Investing in robust network security appliances is a proactive step towards fortifying your organization’s cybersecurity posture in an increasingly interconnected world.
Advantages of Network Security Appliances: Enhancing Network Visibility, Strengthening Security, Streamlining Management, Cost Efficiency, and Scalability
5 Drawbacks of Network Security Appliances: A Comprehensive Analysis
Increased Network Visibility
Increased Network Visibility: Enhancing Security with Network Security Appliances
In the realm of network security, having complete visibility into network traffic is vital for detecting and mitigating potential threats. This is where network security appliances shine, offering a significant advantage in terms of increased network visibility.
Network security appliances provide a single platform that allows administrators to monitor all network traffic in real-time. This comprehensive view enables them to quickly identify any suspicious activity or potential threats lurking within the network. By consolidating monitoring capabilities into a single device, these appliances simplify the task of keeping a watchful eye over the entire network infrastructure.
With network security appliances, administrators can gain insights into various aspects of network traffic, such as the types of applications being used, data transfer volumes, and communication patterns. This level of visibility empowers them to detect anomalies or deviations from normal behavior that could indicate a security breach or unauthorized access attempt.
By leveraging advanced analytics and threat intelligence capabilities, network security appliances can detect known attack signatures and patterns. Administrators can set up alerts and notifications to promptly respond to any identified threats. This proactive approach enables swift action to mitigate risks before they escalate into major incidents.
Moreover, the consolidated view provided by network security appliances simplifies the process of investigating incidents. Instead of sifting through logs from multiple devices or systems, administrators can access all relevant information from a centralised interface. This streamlined approach saves valuable time and resources when identifying the root cause of an incident or conducting forensic analysis.
The increased visibility offered by these appliances also aids in enforcing compliance requirements. Administrators can monitor and track user activities, ensuring adherence to company policies and regulatory standards. It provides an additional layer of protection against insider threats or data breaches caused by negligent or malicious actions from within the organization.
In summary, one notable pro of network security appliances is their ability to enhance network visibility. By providing a consolidated view of all network traffic, these devices empower administrators to quickly identify suspicious activities or potential threats. This proactive approach allows for prompt action, reducing the risk of security breaches and minimizing the impact of incidents. With increased network visibility, organizations can strengthen their overall security posture and ensure the integrity of their digital infrastructure.
Improved Security
Improved Security: Strengthening Your Defenses with Network Security Appliances
In the ever-evolving landscape of cyber threats, businesses must stay one step ahead to protect their sensitive data and infrastructure. Network security appliances offer a powerful solution by enhancing security measures and providing an extra layer of protection against cyber-attacks and data breaches.
One significant advantage of network security appliances is their ability to be configured to block certain types of traffic or enforce specific policies. This level of customization allows businesses to tailor their security measures to match their unique needs and risk profiles. By defining rules and policies, network administrators can control what types of traffic are allowed or denied, ensuring that only legitimate data passes through the network.
This granular control over network traffic helps prevent various cyber threats from infiltrating the system. For example, network security appliances can be configured to block known malicious IP addresses or domains, effectively cutting off communication with potential sources of malware or phishing attempts. By proactively blocking such traffic, these appliances significantly reduce the risk of successful attacks.
Moreover, network security appliances can enforce policies that restrict access to certain websites or applications deemed risky or inappropriate for business purposes. This capability is especially valuable in environments where employees have internet access but need to adhere to strict usage guidelines. By preventing access to potentially harmful websites or unauthorized applications, businesses can mitigate the risks associated with employee negligence or malicious intent.
Network security appliances also play a crucial role in protecting against distributed denial-of-service (DDoS) attacks – a common form of cyber-attack aimed at overwhelming networks with an excessive amount of traffic. These appliances can detect unusual spikes in incoming traffic patterns and automatically take action by diverting or blocking the malicious traffic, ensuring that critical resources remain available for legitimate users.
In addition to blocking malicious traffic and enforcing policies, network security appliances provide comprehensive logging and reporting capabilities. These features allow administrators to monitor network activity closely, identify potential threats or vulnerabilities, and take appropriate actions to mitigate risks. The ability to analyze network traffic and generate detailed reports empowers businesses to make informed decisions about their security strategies and respond promptly to emerging threats.
By incorporating network security appliances into their infrastructure, businesses can strengthen their defenses and create a robust security posture. These appliances act as a proactive barrier against cyber-attacks, preventing unauthorized access and reducing the likelihood of data breaches. With the ability to configure specific rules and policies, businesses can customize their security measures to align with their unique requirements.
In today’s digital landscape, where cyber threats continue to evolve in complexity, network security appliances provide an essential layer of protection. Their ability to block certain types of traffic, enforce policies, and provide comprehensive logging capabilities significantly enhances overall security. By investing in these powerful devices, businesses can fortify their networks against cyber threats and safeguard their valuable assets.
Reduced Management Overhead
Reduced Management Overhead: Streamlining Security with Network Security Appliances
In today’s fast-paced digital landscape, businesses face numerous challenges in managing and maintaining their network security. This is where network security appliances come to the rescue, offering a multitude of benefits to simplify the management process. One significant advantage is the reduced management overhead that these appliances provide.
By consolidating multiple security functions into a single appliance, network security appliances eliminate the need for separate software installations and configurations. This consolidation not only saves time but also reduces the complexity of managing various security components individually.
Traditionally, businesses would have to install and configure separate firewalls, intrusion detection/prevention systems (IDS/IPS), antivirus software, content filtering tools, and more. Each of these components required manual setup and ongoing maintenance, which could be time-consuming and resource-intensive.
With network security appliances, all these functions are integrated into one device. This consolidation not only simplifies the setup process but also streamlines ongoing management. Instead of configuring each component separately, IT administrators can focus on managing a single appliance that handles multiple security functions.
This reduction in manual configuration and maintenance tasks frees up valuable IT resources that can be redirected towards other critical areas of network management or cybersecurity initiatives. IT teams can allocate their time and expertise towards strategic tasks such as threat intelligence analysis, incident response planning, or implementing advanced security measures.
Furthermore, centralizing security management through a network security appliance enables consistent policy enforcement across the entire network infrastructure. Administrators can define unified rules and policies that are applied consistently throughout the organization. This helps ensure that all devices connected to the network receive the same level of protection without any inconsistencies or gaps in security coverage.
Additionally, many network security appliances offer intuitive management interfaces that simplify day-to-day operations. These interfaces often provide comprehensive dashboards displaying real-time information about network traffic, threat alerts, and system health status. Such visibility allows administrators to quickly identify potential issues or threats and take proactive measures to mitigate risks.
In conclusion, network security appliances offer businesses a significant advantage in terms of reduced management overhead. By consolidating multiple security functions into a single device, these appliances simplify the setup, configuration, and ongoing maintenance processes. This not only saves time but also frees up IT resources, allowing them to focus on other critical tasks. With streamlined management, businesses can enhance their overall network security posture and ensure consistent protection across their digital infrastructure.
Cost Savings
Cost Savings: Simplifying Security and Reducing Expenses with Network Security Appliances
In today’s digital landscape, businesses face a constant battle against cyber threats. Protecting sensitive data and securing network infrastructure is crucial, but it can also be costly. This is where network security appliances shine, offering a significant advantage in terms of cost savings.
One of the key benefits of network security appliances is their ability to consolidate multiple security functions into a single device. Instead of purchasing and managing separate products for firewall protection, intrusion detection/prevention, antivirus scanning, content filtering, and more, businesses can streamline their security infrastructure with a single network security appliance.
By combining these functionalities into one device, businesses can achieve substantial cost savings. The initial investment in purchasing and deploying a network security appliance is often less than the combined costs associated with buying individual products for each specific function.
Moreover, managing multiple standalone security solutions can be time-consuming and resource-intensive. Each product may require its own licensing fees, maintenance costs, updates, and dedicated personnel to oversee them. By consolidating these functions into a single appliance, businesses can reduce management complexity and free up resources that can be allocated elsewhere.
Network security appliances also offer long-term cost benefits through improved efficiency. These devices are designed to optimize performance while minimizing resource utilization. For example, they can efficiently process network traffic without causing significant latency or impacting overall network speed. This ensures that businesses can maintain high levels of productivity without sacrificing security or investing in additional hardware.
Additionally, network security appliances often provide scalability options that allow businesses to adapt to changing needs without incurring excessive costs. As your business grows or your security requirements evolve over time, you can easily upgrade or expand the capabilities of your existing appliance rather than investing in entirely new solutions.
It’s worth noting that while the upfront cost savings are evident with network security appliances compared to multiple standalone products, it’s essential to consider the total cost of ownership over the lifespan of the appliance. This includes factors such as maintenance, updates, and support services. However, even when factoring in these costs, network security appliances still generally offer significant savings compared to managing multiple individual products.
In conclusion, network security appliances provide a cost-effective solution for businesses looking to bolster their cybersecurity defenses. By consolidating multiple security functions into a single device, they simplify management, reduce complexity, and offer substantial cost savings compared to deploying and maintaining separate products. Investing in a network security appliance not only protects your business from cyber threats but also ensures that you achieve optimal security while maximizing your budgetary resources.
Scalability
Scalability: Enhancing Network Security with Ease
In today’s dynamic business landscape, organizations are constantly evolving, and so are their network requirements. As networks expand in size and complexity, it becomes crucial to have a scalable security solution that can grow alongside them. Network security appliances offer a significant advantage in this regard, as they can easily be scaled up to meet the needs of an organization without the need for extensive hardware or software replacements.
One of the key benefits of network security appliances is their inherent scalability. These devices are designed to accommodate the increasing demands of a growing network infrastructure without disrupting existing operations. This scalability ensures that organizations can adapt their security measures in line with expanding networks, allowing for seamless growth and enhanced protection.
Unlike traditional security solutions that may require additional hardware or software licenses when scaling up, network security appliances eliminate the need for such investments. Instead, they offer a flexible approach that allows businesses to add more resources or upgrade existing ones within the same appliance framework. This not only simplifies the process but also reduces costs associated with purchasing new equipment or licensing additional software.
By leveraging the scalability of network security appliances, organizations can effectively future-proof their networks. As new devices are added, more users join the network, or data traffic increases, these appliances can be easily upgraded to handle higher workloads and provide robust protection. This ensures that as an organization grows, its network remains secure and resilient against evolving cyber threats.
Another advantage of scalability in network security appliances is its ability to optimize resource utilization. These appliances can allocate resources dynamically based on changing network demands. For example, during periods of high traffic or increased threat activity, additional processing power can be allocated to handle the workload efficiently. Conversely, during periods of lower demand, resources can be reallocated elsewhere to maximize efficiency.
Scalability also simplifies management and reduces complexity in network security infrastructure. With a single appliance capable of scaling up as needed, administrators can easily manage and monitor security measures without the need for multiple devices. This streamlines operations, reduces the risk of misconfigurations, and enhances overall efficiency.
In conclusion, scalability is a significant advantage offered by network security appliances. As organizations expand their network infrastructure, these appliances can seamlessly scale up to meet the growing demands without requiring extensive hardware or software replacements. This flexibility not only saves costs but also future-proofs the network against emerging threats. By leveraging scalable network security appliances, organizations can ensure that their networks remain secure, resilient, and adaptable in an ever-evolving digital landscape.
Cost
Cost: A Consideration in Network Security Appliances
While network security appliances offer invaluable protection for your digital infrastructure, it is important to acknowledge that they come with certain considerations, one of which is cost. Network security appliances can be expensive to purchase and maintain, making it necessary to weigh the financial implications against the benefits they provide.
The initial investment in network security appliances can be significant. High-quality hardware devices with advanced features often come with a price tag that may not be feasible for all businesses, particularly small or budget-constrained organizations. It is essential to carefully assess your specific needs and budgetary constraints before committing to a particular appliance.
In addition to the upfront cost, ongoing maintenance and support expenses should also be taken into account. Network security appliances require regular updates and patches to stay effective against emerging threats. These updates may come at an additional cost, either as part of a subscription or through periodic licensing fees. Furthermore, technical expertise may be required for installation, configuration, and troubleshooting, which could involve hiring dedicated IT staff or outsourcing these services.
However, it is crucial to consider the potential consequences of not investing in robust network security measures. The cost of a cyber attack or data breach can far exceed the expenses associated with purchasing and maintaining network security appliances. A single security incident can lead to financial losses due to stolen data, operational disruptions, reputational damage, legal liabilities, and regulatory penalties.
To mitigate the financial burden associated with network security appliances, businesses have several options. They can explore different vendors and models to find solutions that align with their budget without compromising on essential features. Additionally, some providers offer flexible pricing plans or subscription-based models that allow businesses to scale their investment based on their needs.
Furthermore, considering the total cost of ownership (TCO) rather than just the upfront costs is crucial in evaluating the long-term value of network security appliances. TCO encompasses factors such as maintenance expenses, support services, scalability options, and the potential impact of security incidents. By taking a holistic view, businesses can make more informed decisions regarding their investment in network security.
Ultimately, while the cost of network security appliances is an important consideration, it should not overshadow the critical need for robust cybersecurity measures. The potential consequences of inadequate protection far outweigh the financial investment required. By carefully evaluating your organization’s requirements and exploring cost-effective options, you can strike a balance between budgetary constraints and ensuring the security and integrity of your digital infrastructure.
Remember, investing in network security appliances is an investment in safeguarding your business against cyber threats and protecting your valuable assets.
Complexity
Complexity: The Challenge of Deploying and Managing Network Security Appliances
While network security appliances offer robust protection for your digital infrastructure, it is important to acknowledge that they come with their own set of challenges. One significant drawback is the complexity associated with deploying and managing these devices, which often requires specialist knowledge.
Deploying network security appliances involves a series of intricate steps, including hardware installation, configuration, and integration into the existing network infrastructure. This process can be time-consuming and demanding, particularly for organizations without dedicated IT teams or professionals well-versed in network security.
Furthermore, managing network security appliances requires ongoing monitoring, updates, and maintenance to ensure optimal performance. This responsibility falls on IT administrators or cybersecurity specialists who must possess a deep understanding of the appliance’s functionalities and configurations. Any misconfigurations or oversights could potentially compromise the effectiveness of the security measures.
The complexity arises from the fact that network security appliances often encompass multiple security functions within a single device. Understanding how each component interacts with others and configuring them accordingly can be challenging for those without specialized knowledge in network security.
Moreover, as cyber threats evolve rapidly, keeping up with the latest updates and patches is crucial to maintain an effective defense. Regularly updating firmware and software versions on network security appliances is essential to address newly discovered vulnerabilities or exploit mitigation techniques. Failure to do so can leave your network exposed to emerging threats.
To overcome these challenges, organizations have several options. First, investing in training programs or hiring specialized personnel can help build internal expertise in deploying and managing network security appliances. This ensures that someone within the organization possesses the necessary skills to handle these complex devices effectively.
Alternatively, organizations can consider outsourcing their network security management to third-party providers who specialize in cybersecurity services. These providers have the expertise and resources to handle complex deployments and ongoing management of network security appliances on behalf of their clients.
It is worth noting that while complexity may be a con of network security appliances, it is not an insurmountable obstacle. The benefits of robust protection and comprehensive security outweigh the challenges associated with deployment and management. By investing in the right expertise or partnering with experienced service providers, organizations can navigate the complexities and reap the rewards of a secure network infrastructure.
In conclusion, complexity is a recognized challenge when it comes to deploying and managing network security appliances. However, with the right knowledge, skills, and support, organizations can effectively overcome these hurdles and ensure that their digital infrastructure remains safeguarded against evolving cyber threats.
Performance
Performance: The Trade-Off of Network Security Appliances
While network security appliances are essential for protecting your digital infrastructure, it is important to acknowledge that they can have an impact on network performance. This trade-off between security and performance is a con that businesses must consider when implementing these devices.
Network security appliances are resource-intensive by nature. They require processing power, memory, and network bandwidth to effectively inspect and analyze network traffic in real-time. As a result, the introduction of these devices into a network can potentially lead to decreased performance.
One of the primary factors affecting performance is the additional latency introduced by the appliance. Network traffic needs to be inspected thoroughly before it can pass through the device, which inevitably adds some delay to the overall transmission time. This latency might be negligible for small networks or low-traffic environments but could become more noticeable in larger networks with heavy traffic loads.
The processing power required by security appliances can also impact overall network performance. As these devices analyze each data packet for potential threats, they consume CPU resources. In cases where the appliance is underpowered or overwhelmed by high volumes of traffic, it may struggle to keep up with the demand and cause delays or bottlenecks in data transmission.
Moreover, memory utilization can also affect performance. Network security appliances often store logs and maintain databases of known threats or patterns to enhance their detection capabilities. These databases require memory space, and if not managed efficiently, they can consume valuable resources that could otherwise be used for network operations.
It is important to note that the impact on network performance varies depending on factors such as the size of the network, traffic volume, hardware specifications of the appliance, and configuration settings. Businesses must carefully evaluate their specific requirements and choose an appliance that strikes a balance between robust security features and acceptable performance levels.
Mitigating this con requires careful planning and optimization strategies. Upgrading hardware components such as CPU or memory capacity can help alleviate performance issues caused by resource limitations. Additionally, fine-tuning the configuration settings of the appliance, such as adjusting traffic inspection levels or prioritizing critical applications, can help optimize performance without compromising security.
Businesses should also consider implementing a layered approach to network security. By combining network security appliances with other security measures such as endpoint protection, network segmentation, and traffic prioritization, organizations can distribute the security workload more effectively across their infrastructure. This approach can help alleviate performance concerns by reducing the reliance on a single device to handle all security tasks.
In conclusion, while network security appliances are crucial for protecting your network from cyber threats, it is important to recognize that they can impact performance due to their resource-intensive nature. Businesses must carefully evaluate their specific needs and strike a balance between robust security measures and acceptable performance levels. With proper planning and optimization strategies in place, organizations can effectively mitigate the potential performance drawbacks associated with these devices and maintain a secure and efficient network infrastructure.
Flexibility
Flexibility: A Consideration for Network Security Appliances
While network security appliances offer numerous benefits, it is important to consider potential drawbacks as well. One notable con is the issue of flexibility. Compared to software-based solutions, network security appliances may have limitations when it comes to customization and scalability.
Customization plays a crucial role in adapting security measures to meet specific business requirements. With software-based solutions, organizations often have more flexibility in tailoring the security settings and configurations to their unique needs. This level of customization allows businesses to fine-tune security policies, rules, and protocols according to their specific network environment.
In contrast, network security appliances typically come with preconfigured settings optimized for general use cases. While these default configurations provide a solid foundation for protection, they may not fully align with the specific needs of every organization. Adjusting these settings or implementing custom rules can be more challenging with appliance-based solutions.
Scalability is another aspect where network security appliances may have limitations compared to software-based alternatives. As businesses grow and their network infrastructure expands, they often require additional security measures and resources. Software-based solutions can be more flexible in terms of scaling up or down based on evolving needs.
Network security appliances are physical devices that come with predefined hardware capabilities and capacity limits. Upgrading or expanding these appliances typically involves acquiring new hardware or modules, which can be costly and time-consuming. This lack of scalability may pose challenges for organizations experiencing rapid growth or requiring frequent adjustments to their security infrastructure.
However, it’s important to note that many network security appliance vendors offer different models with varying performance levels and capacities. Organizations can choose an appliance that aligns closely with their current needs while considering future growth projections.
To mitigate the potential inflexibility of network security appliances, businesses should carefully assess their specific requirements before making a decision. Consulting with cybersecurity professionals can help identify the most suitable solution based on factors like customization needs, scalability requirements, budget constraints, and the overall network environment.
In conclusion, while flexibility can be a drawback of network security appliances compared to software-based solutions, it is essential to evaluate this aspect in the context of specific business needs. Network security appliances still provide robust protection and simplify management for many organizations. By understanding their limitations and considering individual requirements, businesses can make informed decisions to ensure an effective and well-rounded security infrastructure.
Maintenance
Maintenance: A Consideration for Network Security Appliances
While network security appliances offer numerous benefits in protecting your digital infrastructure, it is important to consider the maintenance aspect that comes with them. Regular maintenance is required to keep the appliance up-to-date with the latest security patches and features, which can add extra costs to an organization’s IT budget.
Network security appliances, like any other technology, require ongoing updates to address emerging threats and vulnerabilities. These updates may include security patches, firmware upgrades, or software updates that enhance the appliance’s functionality and strengthen its ability to protect against new cyber threats.
The need for regular maintenance means allocating time and resources to ensure that the network security appliance remains current and effective. This can involve scheduling downtime for updates, coordinating with IT staff or external vendors, and potentially disrupting normal network operations during the maintenance window.
In addition to time considerations, there may also be associated costs with maintaining network security appliances. Some vendors charge for ongoing support contracts or subscriptions that provide access to updates and technical assistance. These costs should be factored into an organization’s IT budget when considering the total cost of ownership of network security appliances.
However, it is important to note that while maintenance may require additional resources and incur costs, it is a necessary investment in keeping your network security infrastructure robust and up-to-date. Neglecting regular maintenance can leave your organization vulnerable to new threats or exploits that could have been prevented through timely updates.
To mitigate the impact of maintenance on an organization’s IT budget, careful planning and resource allocation are essential. This includes considering factors such as the scale of your network, the criticality of data being protected, and assessing whether in-house expertise or external support is required for maintenance tasks.
Working closely with trusted vendors or managed service providers can help streamline the maintenance process by providing expert assistance in keeping your network security appliances up-to-date without burdening internal IT teams excessively.
While regular maintenance might add some complexity and cost to the equation, it is a necessary trade-off to ensure that your network security appliances remain effective in today’s rapidly evolving threat landscape. By prioritizing maintenance and staying proactive, organizations can maximize the value and protection provided by these crucial security tools.