Threat Intelligence: Strengthening Your Cybersecurity Defenses
In today’s rapidly evolving digital landscape, cybersecurity has become a top priority for individuals and organizations alike. With the increasing sophistication of cyber threats, it is essential to stay one step ahead in the ongoing battle against malicious actors. This is where threat intelligence comes into play.
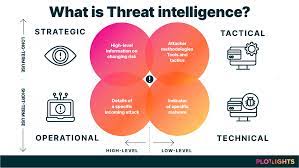
Threat intelligence refers to the knowledge and insights gained from analyzing potential cyber threats. It involves collecting, analyzing, and interpreting data from various sources to identify emerging trends, vulnerabilities, and potential attacks. By understanding the tactics, techniques, and procedures employed by threat actors, organizations can make informed decisions to strengthen their cybersecurity defenses.
One of the primary benefits of threat intelligence is its proactive nature. Instead of waiting for an attack to occur, organizations can leverage threat intelligence to anticipate potential threats and take preventive measures. This proactive approach allows for more effective incident response planning and mitigation strategies.
Threat intelligence encompasses a wide range of data sources. These include open-source information such as public forums and social media platforms, as well as proprietary sources like security vendor reports and industry-specific threat feeds. By aggregating and analyzing this data, organizations gain valuable insights into emerging threats targeting their industry or specific vulnerabilities within their systems.
The key components of an effective threat intelligence program include:
Data Collection: Gathering relevant information from both internal and external sources is crucial. This includes monitoring network logs, analyzing system vulnerabilities, tracking indicators of compromise (IOCs), and keeping up-to-date with security news.
Analysis: Once collected, the data needs to be analyzed by skilled cybersecurity professionals who can identify patterns, trends, and potential risks. This analysis helps in understanding the motives behind attacks and predicting future threats.
Sharing: Collaboration is vital in the fight against cyber threats. Sharing threat intelligence with trusted partners within your industry or sector allows for a broader perspective on emerging risks while fostering a collective defense approach.
Integration: Threat intelligence should be integrated into existing security systems and processes to ensure a proactive response. This can involve automating the identification and blocking of known threats, as well as updating security policies and procedures based on the latest intelligence.
By implementing a robust threat intelligence program, organizations can significantly enhance their cybersecurity posture. Here are some of the key benefits:
Early Detection: Threat intelligence enables organizations to identify potential threats at an early stage, allowing them to take immediate action to prevent or mitigate attacks.
Improved Incident Response: With timely and accurate threat intelligence, incident response teams can make informed decisions and respond effectively in the event of a cyber incident.
Enhanced Risk Management: Understanding the specific threats targeting your organization helps in prioritizing security measures and allocating resources where they are most needed.
Regulatory Compliance: Many industries have specific compliance requirements related to cybersecurity. By leveraging threat intelligence, organizations can better meet these standards and protect sensitive data.
Competitive Advantage: Organizations that prioritize threat intelligence gain a competitive edge by staying ahead of cybercriminals, protecting their reputation, and maintaining customer trust.
In conclusion, threat intelligence is an indispensable tool in today’s cybersecurity landscape. By leveraging the power of data analysis and collaboration, organizations can proactively identify and mitigate potential cyber threats before they cause significant damage. Investing in a comprehensive threat intelligence program not only strengthens your defenses but also demonstrates your commitment to safeguarding sensitive information in an increasingly interconnected world.
9 Essential Tips for Effective Threat Intelligence in Your Organisation (English UK)
- Ensure your threat intelligence is up-to-date and relevant to your organisation.
- Identify the key sources of threat intelligence and ensure they are monitored regularly.
- Develop a process for collecting, analysing and disseminating threat intelligence information within your organisation.
- Utilise open source intelligence (OSINT) sources to gain additional insight into threats targeting you or similar organisations in the same sector/industry as you.
- Establish relationships with other security professionals who can provide additional valuable insights into potential threats facing your organisation or industry sector as a whole.
- Investigate any suspicious activity that could indicate a potential attack on your network or systems, such as unusual traffic patterns or changes in user behaviour, and take appropriate action if necessary.
- Use automated tools to help identify anomalies in data that may indicate malicious activity or potential threats against you or other organisations in the same industry sector as you; these tools can be used to supplement manual analysis of the data collected by security personnel within an organisation
- Ensure all staff are aware of their responsibility when it comes to reporting any suspicious activity they have identified so that it can be investigated further by security personnel within the organisation
- Review existing policies and procedures regularly to ensure they remain effective at mitigating potential threats identified through threat intelligence gathering activities
Ensure your threat intelligence is up-to-date and relevant to your organisation.
Ensure Your Threat Intelligence is Up-to-Date and Relevant to Your Organization
In the ever-evolving world of cybersecurity, staying ahead of potential threats is crucial. One key tip to bolster your defenses is to ensure that your threat intelligence is up-to-date and relevant to your organization. Here’s why this is so important.
Threat intelligence provides valuable insights into the latest tactics, techniques, and procedures employed by cybercriminals. By keeping your threat intelligence up-to-date, you can stay informed about emerging threats that may target your organization specifically. This allows you to proactively identify vulnerabilities within your systems and take appropriate measures to mitigate them.
Outdated threat intelligence can be as good as no intelligence at all. Cybercriminals constantly adapt their methods, making use of new attack vectors and exploiting emerging vulnerabilities. If you rely on outdated information, you may be blindsided by new types of attacks that your security measures are ill-equipped to handle.
Relevance is another critical aspect of effective threat intelligence. Not all threats are equal, and not all threats pose the same level of risk to every organization. By ensuring that your threat intelligence aligns with your organization’s specific industry, size, and technology infrastructure, you can focus on the threats that are most likely to affect you.
To keep your threat intelligence up-to-date and relevant:
- Regularly Monitor Sources: Stay connected with trusted sources such as cybersecurity blogs, industry-specific reports, security vendor updates, and government advisories. These sources often provide timely information about emerging threats and recommended countermeasures.
- Collaborate with Peers: Engage in information-sharing initiatives with other organizations in your industry or sector. Participating in forums or joining threat-sharing communities allows you to benefit from collective knowledge and gain insights into potential risks that others may have already encountered.
- Leverage Automated Tools: Utilize automated tools that aggregate real-time threat data from various sources. These tools can help streamline the process of collecting and analyzing threat intelligence, providing you with actionable insights quickly.
- Engage with Security Vendors: Work closely with your security vendors to ensure that you receive timely updates on new threats and vulnerabilities. They can provide you with the latest patches, signatures, or software updates to protect your systems.
By prioritizing up-to-date and relevant threat intelligence, you can stay ahead of cyber threats and minimize the risk of a successful attack. Regularly reviewing and updating your threat intelligence strategy will help ensure that your organization remains resilient in the face of evolving cybersecurity challenges. Remember, knowledge is power when it comes to protecting your digital assets.
Identify the key sources of threat intelligence and ensure they are monitored regularly.
Identifying and Monitoring Key Sources of Threat Intelligence
In the ever-changing world of cybersecurity, staying updated on the latest threats is crucial to maintaining a strong defense. One essential tip for effective threat intelligence is to identify and monitor the key sources of information regularly.
Threat intelligence comes from a variety of sources, both internal and external. Internal sources include network logs, system vulnerability assessments, and incident reports from previous attacks. These sources provide valuable insights into potential weaknesses within your own infrastructure.
External sources, on the other hand, offer a broader view of the threat landscape. These include security vendor reports, industry-specific threat feeds, open-source intelligence (OSINT), and even public forums or social media platforms where cybercriminals may discuss their activities.
To effectively harness threat intelligence, it is important to identify the most relevant and reliable sources for your organization. This can vary depending on your industry, size, and specific security concerns. For example, financial institutions may prioritize monitoring financial crime forums or malware campaigns targeting banks.
Once you have identified these key sources, it is crucial to establish a regular monitoring routine. Cyber threats are constantly evolving, so keeping up-to-date with the latest information is vital. Set up automated systems or dedicated personnel to regularly review and analyze data from these sources.
Regular monitoring allows you to stay ahead of emerging threats by identifying new attack vectors or patterns that could impact your organization’s security posture. It enables you to proactively implement preventive measures or update existing defenses based on the latest intelligence.
Moreover, monitoring key sources of threat intelligence helps in early detection of potential risks. By promptly identifying indicators of compromise (IOCs) or signs of malicious activity reported by trusted sources, you can take immediate action to mitigate any potential damage before it escalates into a full-blown cyber attack.
Remember that threat intelligence is not a one-time task but an ongoing process that requires continuous effort and attention. By regularly monitoring key sources of threat intelligence, you can stay informed about the latest threats, adapt your security measures accordingly, and enhance your organization’s overall cybersecurity posture.
In conclusion, identifying and monitoring key sources of threat intelligence is a fundamental tip for effective cybersecurity. By understanding where to gather relevant information and consistently reviewing it, you can proactively protect your organization from emerging threats and maintain a robust defense against cybercriminals. Stay vigilant, stay informed, and stay secure.
Develop a process for collecting, analysing and disseminating threat intelligence information within your organisation.
Developing a Process for Effective Threat Intelligence Management
In today’s ever-evolving cybersecurity landscape, it is essential for organizations to stay proactive in the face of emerging threats. One crucial tip for bolstering your cybersecurity defenses is to develop a well-defined process for collecting, analyzing, and disseminating threat intelligence information within your organization.
Collecting relevant threat intelligence data is the first step towards building a strong defense. This involves monitoring various sources such as security feeds, industry reports, open-source intelligence, and internal network logs. By gathering this information, organizations can gain insights into potential vulnerabilities and emerging attack trends specific to their industry or systems.
Once the data is collected, it should be subjected to thorough analysis by skilled cybersecurity professionals. This analysis helps in identifying patterns, trends, and potential risks that may pose a threat to your organization’s security. By understanding the motives behind attacks and the tactics employed by threat actors, you can make informed decisions on how best to protect your systems.
Disseminating threat intelligence information effectively within your organization is equally important. This involves sharing relevant insights with key stakeholders such as IT teams, incident response teams, senior management, and even employees at large. By ensuring that everyone has access to up-to-date threat intelligence information, you create a culture of awareness and empowerment throughout the organization.
Developing a process for disseminating threat intelligence also includes defining clear roles and responsibilities within your organization. Assign individuals or teams who will be responsible for monitoring threats, analyzing data, and disseminating actionable intelligence. This ensures that there is accountability and efficiency in handling potential risks.
Automation can also play a significant role in streamlining the process of threat intelligence management. Implementing technologies that automate data collection, analysis, and dissemination can save time and resources while allowing for real-time updates on emerging threats.
By developing a robust process for collecting, analyzing, and disseminating threat intelligence information within your organization, you empower yourself with valuable insights to make informed decisions and take proactive measures to protect your systems. This process ensures that you stay one step ahead of potential threats, allowing you to mitigate risks effectively and safeguard sensitive data.
Remember, cybersecurity is a collective effort, and threat intelligence is a powerful tool in the fight against cyber threats. By investing time and resources into developing an effective process for managing threat intelligence, you demonstrate your commitment to maintaining a strong security posture and protecting your organization from evolving cyber risks.
Utilise open source intelligence (OSINT) sources to gain additional insight into threats targeting you or similar organisations in the same sector/industry as you.
Harnessing Open Source Intelligence (OSINT) for Enhanced Threat Intelligence
In the realm of cybersecurity, knowledge is power. Understanding the threats that target your organization or industry is crucial for effective defense. One valuable source of information that can provide additional insights is Open Source Intelligence (OSINT). By utilizing OSINT sources, you can gain a deeper understanding of the threats targeting you or similar organizations within your sector or industry.
Open Source Intelligence refers to publicly available information from sources such as social media platforms, online forums, news articles, and other publicly accessible resources. It provides a wealth of data that can be analyzed to identify potential threats and trends.
When it comes to threat intelligence, OSINT serves as a valuable supplement to existing internal data sources. By incorporating OSINT into your threat intelligence program, you can gain several advantages:
Expanding Your Knowledge: OSINT sources provide a broader perspective on threats targeting your organization or industry. They offer insights into emerging attack techniques, vulnerabilities, and indicators of compromise that may not be readily available through traditional channels.
Identifying Targeted Campaigns: Through OSINT analysis, you can uncover information about targeted campaigns launched by threat actors against organizations similar to yours. This knowledge enables you to proactively prepare for potential attacks and implement necessary security measures.
Monitoring Online Discussions: By monitoring relevant online forums and social media platforms, you can gain insights into discussions related to your industry’s cybersecurity challenges. This allows you to stay informed about emerging threats and adapt your security strategy accordingly.
Tracking Threat Actor Activities: OSINT sources enable you to keep tabs on the activities of known threat actors or hacking groups operating in your sector or industry. Understanding their tactics, techniques, and procedures helps in identifying potential risks and preparing appropriate defenses.
To effectively utilize OSINT for threat intelligence:
Identify Relevant Sources: Determine which OSINT sources are most relevant to your organization or industry. This could include industry-specific forums, social media groups, or news outlets that frequently report on cybersecurity issues.
Establish Monitoring Mechanisms: Set up automated tools or manual processes to monitor these sources regularly. This ensures that you stay up-to-date with the latest information and potential threats.
Analyze and Validate Information: Once collected, analyze the OSINT data to identify patterns, trends, and potential risks. It is important to validate the accuracy and credibility of the information obtained from these sources before taking any action.
Collaborate and Share Insights: Engage with trusted partners within your industry or sector to share OSINT findings and collaborate on threat intelligence. This collective approach strengthens defenses across the board.
By incorporating OSINT into your threat intelligence strategy, you can gain valuable insights into threats targeting your organization or similar entities in your industry. This knowledge empowers you to take proactive measures, strengthen your cybersecurity defenses, and effectively mitigate potential risks. Stay informed, stay vigilant, and leverage the power of Open Source Intelligence for enhanced threat intelligence capabilities.
Establish relationships with other security professionals who can provide additional valuable insights into potential threats facing your organisation or industry sector as a whole.
Building Strong Connections: The Power of Collaboration in Threat Intelligence
In the ever-evolving world of cybersecurity, staying ahead of potential threats is of paramount importance. While implementing robust security measures within your organization is crucial, it is equally vital to establish relationships with other security professionals who can provide valuable insights into potential threats facing your organization or industry sector as a whole. This collaborative approach is known as threat intelligence sharing, and it can significantly enhance your cybersecurity defenses.
Threat intelligence sharing involves establishing trusted connections with other security experts, both within and outside your organization. By exchanging information and insights about emerging threats, attack techniques, and vulnerabilities, you gain a broader perspective on the evolving threat landscape. This collaborative effort helps to identify potential risks early on and develop effective mitigation strategies.
The benefits of establishing relationships with other security professionals for threat intelligence are numerous:
Expanded Knowledge Base: By connecting with others in the cybersecurity community, you tap into a wealth of knowledge and expertise. Each individual brings their unique experiences and insights, providing you with a broader understanding of potential threats.
Industry-Specific Insights: Collaborating with professionals from your industry sector allows you to focus on threats that are most relevant to your organization. Sharing information about targeted attacks or specific vulnerabilities within your sector helps everyone stay prepared.
Early Warning System: Through ongoing communication and information exchange, you create an early warning system for emerging threats. When one member detects a new attack vector or identifies a malicious campaign, they can alert others in the network promptly.
Validation of Threats: By sharing threat intelligence with trusted peers, you can validate the credibility and severity of potential threats. This helps in prioritizing response efforts and allocating resources effectively.
Improved Incident Response: In the event of a cyber incident, having established relationships with other security professionals can be invaluable. Their expertise and guidance can assist in formulating an effective response strategy, minimizing the impact of the attack.
Collaborative Defense: Threat intelligence sharing promotes a collective defense approach. By working together, organizations can pool their resources, knowledge, and capabilities to create a stronger front against cyber threats.
To establish relationships with other security professionals for threat intelligence sharing, consider participating in industry-specific forums, conferences, and online communities. Engage in discussions, share your experiences, and actively seek out opportunities to connect with like-minded individuals. Additionally, joining threat intelligence-sharing platforms or organizations can provide structured frameworks for collaboration.
Remember that trust and confidentiality are paramount when sharing threat intelligence. Ensure that you establish clear guidelines and agreements regarding the handling of sensitive information and adhere to any legal or regulatory requirements.
In conclusion, establishing relationships with other security professionals for threat intelligence sharing is a proactive step towards strengthening your cybersecurity defenses. By collaborating with trusted peers, you gain valuable insights into potential threats facing your organization or industry sector as a whole. Together, we can create a more resilient cybersecurity ecosystem that protects us all from evolving cyber threats.
Investigate any suspicious activity that could indicate a potential attack on your network or systems, such as unusual traffic patterns or changes in user behaviour, and take appropriate action if necessary.
Safeguard Your Network: Investigate Suspicious Activity with Threat Intelligence
In the ever-evolving landscape of cybersecurity, it’s crucial to remain vigilant and proactive in protecting your network and systems from potential attacks. One valuable tip to bolster your defenses is to investigate any suspicious activity that could indicate a looming threat. By closely monitoring and analyzing unusual traffic patterns or changes in user behavior, you can swiftly identify potential attacks and take appropriate action.
Suspicious activity can manifest in various forms, such as a sudden surge in network traffic from unexpected sources, unusual login attempts, or abnormal user behavior patterns. These anomalies may be indicative of malicious actors attempting to breach your network or compromise your systems.
To effectively investigate suspicious activity, incorporating threat intelligence is essential. By leveraging up-to-date threat intelligence feeds and tools, you gain access to valuable information about emerging threats and attack techniques. This knowledge empowers you to recognize patterns associated with known attack vectors and identify potential risks more efficiently.
When investigating suspicious activity, it’s crucial to follow a systematic approach:
- Monitor Network Traffic: Utilize network monitoring tools to track incoming and outgoing traffic. Keep an eye out for any sudden spikes or unusual patterns that deviate from normal network behavior.
- Analyze User Behavior: Regularly review user activity logs and compare them against established baselines. Look for any significant deviations that could indicate unauthorized access or compromised accounts.
- Employ Behavioural Analytics: Implement behavioural analytics solutions that leverage machine learning algorithms to detect anomalies in user behavior. These tools can help identify potential insider threats or compromised accounts exhibiting unusual actions.
- Collaborate with Threat Intelligence Sources: Stay connected with trusted threat intelligence sources that provide real-time updates on emerging threats and attack campaigns relevant to your industry or sector.
- Take Immediate Action: If suspicious activity is detected, act promptly based on the severity of the threat. This may involve isolating affected systems, blocking malicious IP addresses, resetting compromised user accounts, or escalating the incident to your incident response team.
By promptly investigating and responding to suspicious activity, you can minimize the potential impact of a cyber attack and mitigate any vulnerabilities within your network or systems. Remember that prevention is always better than cure when it comes to cybersecurity.
Incorporating threat intelligence into your security strategy equips you with the knowledge and tools necessary to identify potential threats early on. By staying proactive and responsive, you can effectively safeguard your network from cyber threats and maintain the integrity of your systems in an increasingly interconnected world.
Use automated tools to help identify anomalies in data that may indicate malicious activity or potential threats against you or other organisations in the same industry sector as you; these tools can be used to supplement manual analysis of the data collected by security personnel within an organisation
Harnessing the Power of Automation: Unleashing Threat Intelligence Tools
In today’s digital landscape, where cyber threats are constantly evolving, organizations must be proactive in defending against potential attacks. One effective approach is to leverage automated tools that assist in identifying anomalies within data, which may indicate malicious activity or potential threats. These tools act as a supplement to the manual analysis conducted by security personnel within an organization.
The volume and complexity of data generated by modern systems can overwhelm even the most skilled security professionals. This is where automated threat intelligence tools come into play. By harnessing the power of automation, organizations can efficiently analyze vast amounts of data and detect patterns that may be indicative of malicious intent.
These tools utilize advanced algorithms to identify anomalies within data sets, allowing for early detection and swift response to potential threats. By continuously monitoring network logs, system vulnerabilities, and other relevant sources of information, these tools can alert security personnel to suspicious activities that may have otherwise gone unnoticed.
One significant advantage of using automated threat intelligence tools is their ability to provide real-time analysis. This means that as new data is collected, it is immediately processed and compared against known threat indicators. This proactive approach enables organizations to respond swiftly to emerging threats before they have a chance to cause significant damage.
Moreover, these tools are designed to complement manual analysis conducted by security personnel. While human expertise is invaluable in understanding the context and nuances of potential threats, automation can significantly enhance their capabilities by processing large volumes of data quickly and accurately.
By integrating automated threat intelligence tools into their cybersecurity infrastructure, organizations gain several benefits:
Improved Efficiency: Automated tools can process vast amounts of data much faster than manual analysis alone. This frees up valuable time for security personnel to focus on more complex tasks that require human intervention.
Enhanced Accuracy: Automation reduces the risk of human error often associated with manual analysis. By leveraging algorithms designed specifically for threat detection, organizations can achieve a higher level of accuracy in identifying potential threats.
Early Threat Detection: By continuously monitoring data and identifying anomalies in real-time, automated tools enable organizations to detect potential threats at an early stage. This allows for immediate action to be taken, minimizing the impact of an attack.
Scalability: As organizations grow and generate more data, manual analysis becomes increasingly challenging. Automated tools can easily scale to handle larger volumes of data without compromising accuracy or efficiency.
In conclusion, leveraging automated threat intelligence tools is crucial in today’s rapidly evolving cybersecurity landscape. By using these tools to supplement manual analysis conducted by security personnel, organizations can effectively identify anomalies within data that may indicate malicious activity or potential threats. This proactive approach enhances efficiency, accuracy, and early threat detection capabilities. Embracing automation empowers organizations to stay one step ahead in the ongoing battle against cyber threats and protect their valuable assets from harm.
Ensure all staff are aware of their responsibility when it comes to reporting any suspicious activity they have identified so that it can be investigated further by security personnel within the organisation
Promoting a Culture of Vigilance: The Importance of Staff Awareness in Threat Intelligence
In the realm of cybersecurity, every member of an organization plays a crucial role in maintaining a robust defense against potential threats. One key tip to bolster your threat intelligence efforts is to ensure that all staff are aware of their responsibility when it comes to reporting any suspicious activity they have identified. By encouraging a culture of vigilance and promoting active participation in threat detection, organizations can effectively strengthen their overall security posture.
In today’s digital landscape, cyber threats can come from various sources and take on different forms. From phishing emails to social engineering tactics, malicious actors constantly seek opportunities to exploit vulnerabilities within an organization’s systems or gain unauthorized access to sensitive information. This is where the power of staff awareness becomes paramount.
When employees are educated about the signs of suspicious activity and understand their role in reporting such incidents, it creates an additional layer of defense. By empowering staff members to be proactive observers, organizations can tap into a valuable resource for threat intelligence.
Encouraging staff to report any unusual or suspicious activity they encounter serves multiple purposes. Firstly, it allows for timely investigation by security personnel within the organization. Promptly addressing potential threats can help prevent further damage or unauthorized access before it escalates into a major incident.
Secondly, by involving staff in the reporting process, organizations gain a broader perspective on potential threats. Employees across various departments may notice patterns or trends that could be missed by automated systems or dedicated security teams alone. Their insights can provide valuable context and assist in identifying emerging risks.
To ensure effective implementation, organizations should provide regular cybersecurity training sessions that educate staff on what constitutes suspicious activity and how to report it securely. This training should cover common red flags such as unexpected requests for sensitive information, unusual system behavior, or unrecognized devices on the network.
Additionally, organizations should establish clear reporting channels and protocols so that employees know exactly how and where to report suspicious activity. Encouraging open communication and fostering a non-punitive reporting culture will help alleviate any concerns employees may have about reporting incidents.
By prioritizing staff awareness and active participation in threat intelligence efforts, organizations can significantly enhance their overall security posture. Employees become an integral part of the defense mechanism, acting as the first line of defense against potential threats. This collective effort strengthens the organization’s ability to detect, investigate, and mitigate any potential risks effectively.
In conclusion, ensuring that all staff members are aware of their responsibility to report any suspicious activity they identify is a vital tip for successful threat intelligence implementation. By promoting a culture of vigilance and providing the necessary training and support, organizations can tap into the collective knowledge and observations of their employees, bolstering their cybersecurity defenses and staying one step ahead of potential threats.
Review existing policies and procedures regularly to ensure they remain effective at mitigating potential threats identified through threat intelligence gathering activities
Regular Policy and Procedure Reviews: Strengthening Your Cybersecurity with Threat Intelligence
In the ever-changing world of cybersecurity, it is crucial to stay one step ahead of potential threats. One effective way to achieve this is by regularly reviewing existing policies and procedures to ensure they remain effective at mitigating the risks identified through threat intelligence gathering activities.
Threat intelligence provides valuable insights into emerging threats, vulnerabilities, and attack techniques. By leveraging this knowledge, organizations can proactively update their policies and procedures to address the evolving threat landscape.
Regular reviews help identify any gaps or weaknesses in current security measures. It allows organizations to assess whether their policies align with the latest threat intelligence findings and industry best practices. By doing so, they can make necessary adjustments to enhance their cybersecurity defenses.
During policy and procedure reviews, organizations should consider the following key aspects:
Relevance: Are the existing policies still applicable in light of new threats? Do they cover all potential attack vectors identified through threat intelligence? Regular reviews ensure that policies remain relevant and up-to-date.
Effectiveness: Do the procedures effectively mitigate the risks highlighted by threat intelligence? Are there any new techniques or vulnerabilities that need to be addressed? Regular reviews help identify areas where improvements are needed.
Compliance: Are the policies aligned with regulatory requirements? Compliance standards evolve over time, so it is essential to review policies regularly to ensure ongoing adherence.
Awareness: Are employees aware of existing policies and procedures? Regular reviews provide an opportunity to reinforce awareness training and ensure that employees understand their roles in maintaining a secure environment.
By conducting regular policy and procedure reviews, organizations can adapt quickly to emerging threats. This proactive approach enables them to implement necessary changes promptly, reducing the likelihood of successful cyberattacks.
Moreover, regular reviews demonstrate a commitment to continuous improvement in cybersecurity. They show stakeholders that an organization is actively monitoring the threat landscape and taking steps to enhance its security measures. This can help build trust with customers, partners, and regulatory bodies.
In conclusion, regular policy and procedure reviews are essential for maintaining robust cybersecurity defenses. By aligning policies with threat intelligence findings, organizations can effectively mitigate potential risks. Embracing a proactive approach to cybersecurity ensures that policies remain relevant, effective, and compliant with evolving threats and regulatory requirements. Stay vigilant, review regularly, and strengthen your cybersecurity posture in the face of an ever-evolving digital landscape.