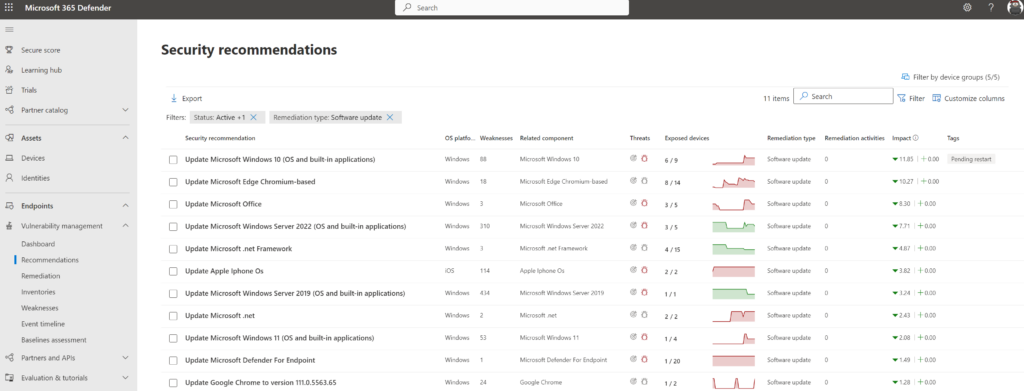
The Importance of Vulnerability Management Defender for Endpoint
In today’s digital landscape, the security of endpoints is more critical than ever. With the increasing number of cyber threats targeting devices such as laptops, desktops, and mobile phones, having a robust vulnerability management defender for endpoint is essential.
Endpoint security solutions play a crucial role in protecting devices from malware, ransomware, and other malicious attacks. However, simply having antivirus software is not enough. To effectively safeguard your endpoints, you need a comprehensive vulnerability management defender that can identify and patch security vulnerabilities before they are exploited by cybercriminals.
A vulnerability management defender for endpoint works by continuously scanning devices for weaknesses in software applications, operating systems, and configurations. By proactively identifying vulnerabilities, IT teams can take prompt action to remediate these issues and reduce the risk of a successful cyber attack.
Furthermore, a robust vulnerability management defender provides real-time visibility into the security posture of endpoints across your network. This visibility allows IT administrators to prioritise remediation efforts based on the severity of vulnerabilities and the level of risk they pose to the organisation.
Implementing a vulnerability management defender for endpoint is not only about protecting your devices; it is also about safeguarding your data and ensuring business continuity. By staying ahead of emerging threats and keeping your endpoints secure, you can minimise the impact of cyber attacks and maintain the trust of your customers and stakeholders.
In conclusion, investing in a vulnerability management defender for endpoint is a proactive measure that can significantly enhance your organisation’s cybersecurity posture. By leveraging advanced technologies to detect and mitigate vulnerabilities on endpoints, you can fortify your defences against evolving cyber threats and stay one step ahead of malicious actors.
Essential Tips for Effective Vulnerability Management in Endpoint Defence
- Regularly scan endpoints for vulnerabilities using a reliable vulnerability scanner.
- Prioritize patching based on the severity of vulnerabilities to mitigate high-risk threats first.
- Ensure all endpoint security software is up to date to defend against known vulnerabilities.
- Implement network segmentation to contain potential breaches and limit the impact of attacks.
- Train employees on cybersecurity best practices to reduce the risk of human error leading to vulnerabilities.
- Utilize endpoint protection platforms with threat intelligence capabilities for proactive defence against emerging threats.
- Establish a response plan for incidents involving vulnerable endpoints, including isolation and remediation procedures.
- Regularly review and update vulnerability management policies and procedures to adapt to evolving cyber threats.
- Monitor endpoint activity for signs of compromise or unusual behaviour that may indicate a vulnerability has been exploited.
Regularly scan endpoints for vulnerabilities using a reliable vulnerability scanner.
To enhance the security of your endpoints, it is crucial to regularly scan them for vulnerabilities using a trusted vulnerability scanner. By conducting routine scans, you can identify weaknesses in software applications, operating systems, and configurations that could be exploited by cybercriminals. A reliable vulnerability management defender for endpoint will help you stay proactive in addressing potential security risks, enabling you to patch vulnerabilities promptly and strengthen the overall resilience of your network against cyber threats.
Prioritize patching based on the severity of vulnerabilities to mitigate high-risk threats first.
When it comes to vulnerability management defender for endpoint, prioritising patching based on the severity of vulnerabilities is crucial in mitigating high-risk threats effectively. By focusing on addressing the most critical vulnerabilities first, organisations can significantly reduce the likelihood of cyber attacks exploiting these weaknesses. This strategic approach ensures that resources are allocated efficiently to tackle the most pressing security concerns, thereby strengthening the overall resilience of endpoint devices and enhancing the organisation’s cybersecurity posture.
Ensure all endpoint security software is up to date to defend against known vulnerabilities.
To enhance the effectiveness of your vulnerability management defender for endpoint, it is crucial to ensure that all endpoint security software is kept up to date. By regularly updating antivirus programs, firewalls, and other security tools, you can defend against known vulnerabilities and strengthen your overall cybersecurity posture. Updating endpoint security software not only patches existing vulnerabilities but also equips your devices with the latest threat intelligence to detect and prevent emerging cyber threats. Stay vigilant in maintaining the currency of your security software to maximise protection for your endpoints and safeguard your digital assets.
Implement network segmentation to contain potential breaches and limit the impact of attacks.
Implementing network segmentation is a crucial tip in vulnerability management defender for endpoint. By dividing your network into separate segments, you can contain potential breaches and limit the impact of attacks. This strategy restricts the lateral movement of threats within your network, making it more challenging for cybercriminals to access sensitive data or compromise critical systems. Network segmentation enhances overall security by isolating vulnerable endpoints and creating barriers that prevent attackers from easily moving laterally across the network. By implementing this proactive measure, organisations can strengthen their defences and mitigate the risks associated with cyber threats.
Train employees on cybersecurity best practices to reduce the risk of human error leading to vulnerabilities.
Training employees on cybersecurity best practices is a crucial step in enhancing the effectiveness of a vulnerability management defender for endpoint. By educating staff on how to recognise and respond to potential security threats, organisations can significantly reduce the risk of human error leading to vulnerabilities. Empowering employees with the knowledge and skills to identify phishing attempts, avoid suspicious links, and follow secure password practices can create a culture of security awareness that strengthens the overall cybersecurity posture of the organisation.
Utilize endpoint protection platforms with threat intelligence capabilities for proactive defence against emerging threats.
To enhance your organisation’s cybersecurity strategy, it is recommended to leverage endpoint protection platforms that incorporate threat intelligence capabilities. By utilising these advanced tools, you can proactively defend your endpoints against emerging threats. Threat intelligence provides valuable insights into the latest cyber threats and attack trends, enabling you to stay one step ahead of cybercriminals. By integrating threat intelligence into your vulnerability management defender for endpoint, you can strengthen your defences and mitigate potential risks before they escalate.
Establish a response plan for incidents involving vulnerable endpoints, including isolation and remediation procedures.
Establishing a response plan for incidents involving vulnerable endpoints is a crucial aspect of effective vulnerability management defender for endpoint. By outlining clear isolation and remediation procedures in advance, organisations can swiftly contain and address security breaches on endpoints. In the event of an incident, having a well-defined response plan ensures that IT teams can act promptly to mitigate the impact, minimise potential damage, and restore the affected endpoints to a secure state. Proactive planning and preparedness are key to effectively managing vulnerabilities and maintaining the overall security of endpoint devices.
Regularly review and update vulnerability management policies and procedures to adapt to evolving cyber threats.
It is crucial to regularly review and update vulnerability management policies and procedures to adapt to the ever-evolving landscape of cyber threats. By staying vigilant and proactive in assessing and refining your vulnerability management practices, you can ensure that your endpoint security remains effective against emerging risks. Regular updates to policies and procedures enable your organisation to stay ahead of cybercriminals, mitigate vulnerabilities promptly, and strengthen your overall cybersecurity posture. Embracing a culture of continuous improvement in vulnerability management is key to safeguarding your endpoints and data from evolving threats in today’s digital environment.
Monitor endpoint activity for signs of compromise or unusual behaviour that may indicate a vulnerability has been exploited.
To enhance the effectiveness of your vulnerability management defender for endpoints, it is crucial to monitor endpoint activity diligently. By keeping a close eye on the behaviour of devices within your network, you can quickly detect signs of compromise or unusual activities that may indicate a vulnerability has been exploited. Proactively monitoring endpoint activity allows you to respond promptly to potential security breaches, investigate suspicious behaviour, and take necessary actions to mitigate risks before they escalate. This proactive approach strengthens your overall cybersecurity posture and helps safeguard your organisation’s sensitive data and assets from malicious threats.