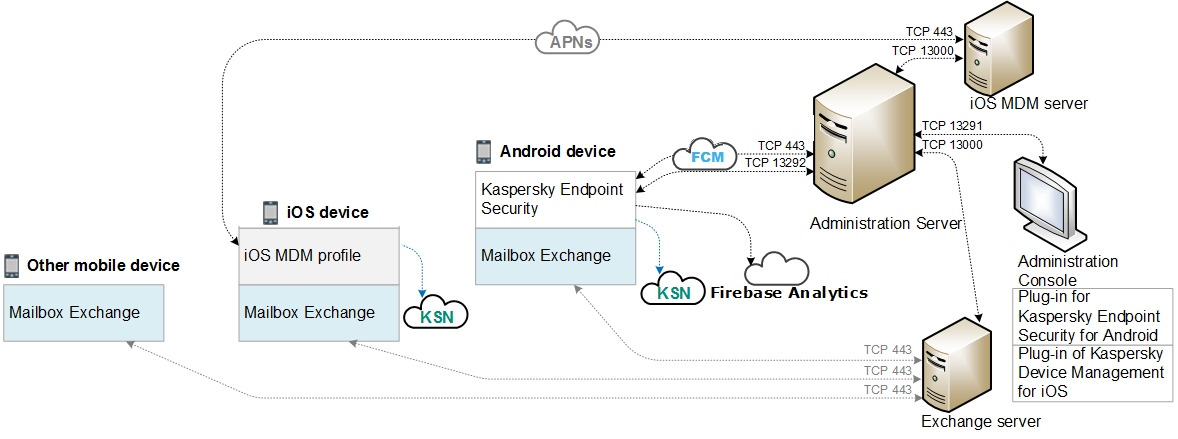
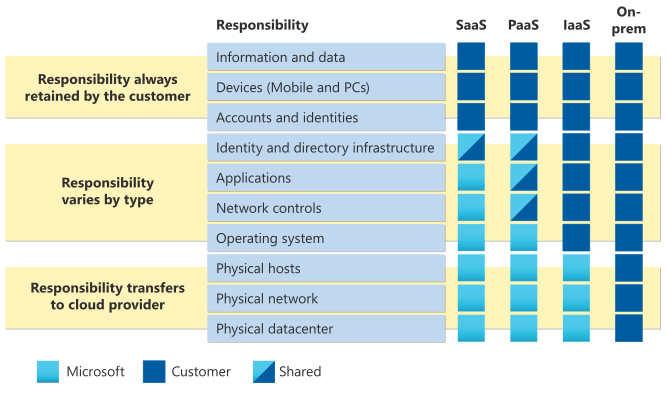
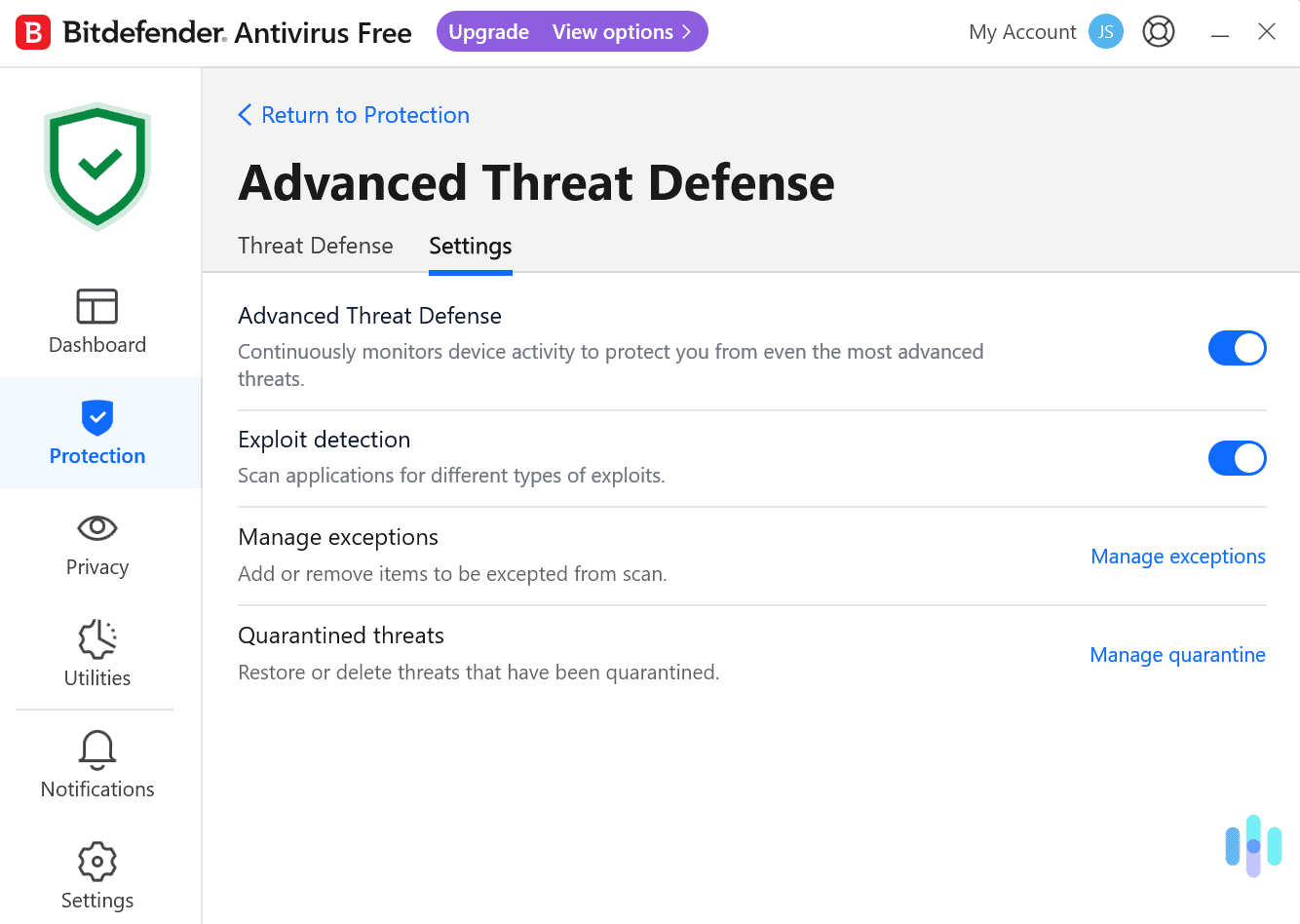
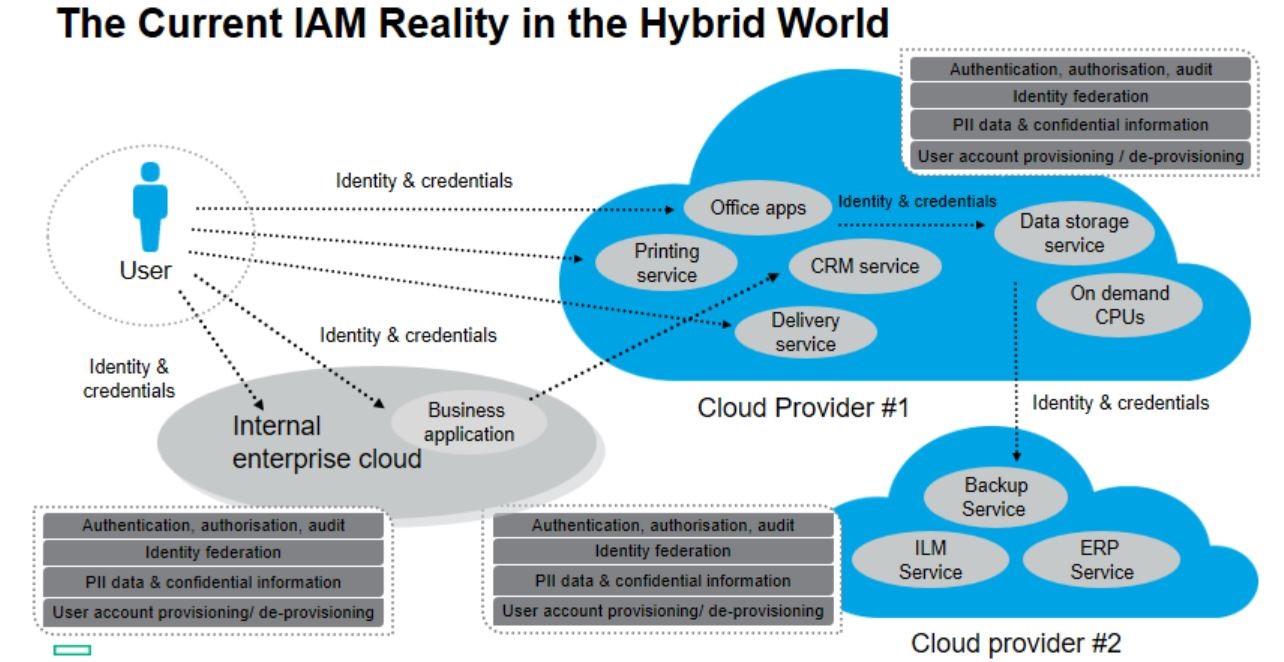
Enhancing Business Security with Kaspersky Endpoint Security and Management
Kaspersky Endpoint Security and Management Kaspersky Endpoint Security and Management Kaspersky Endpoint Security and Management…
0 Comments