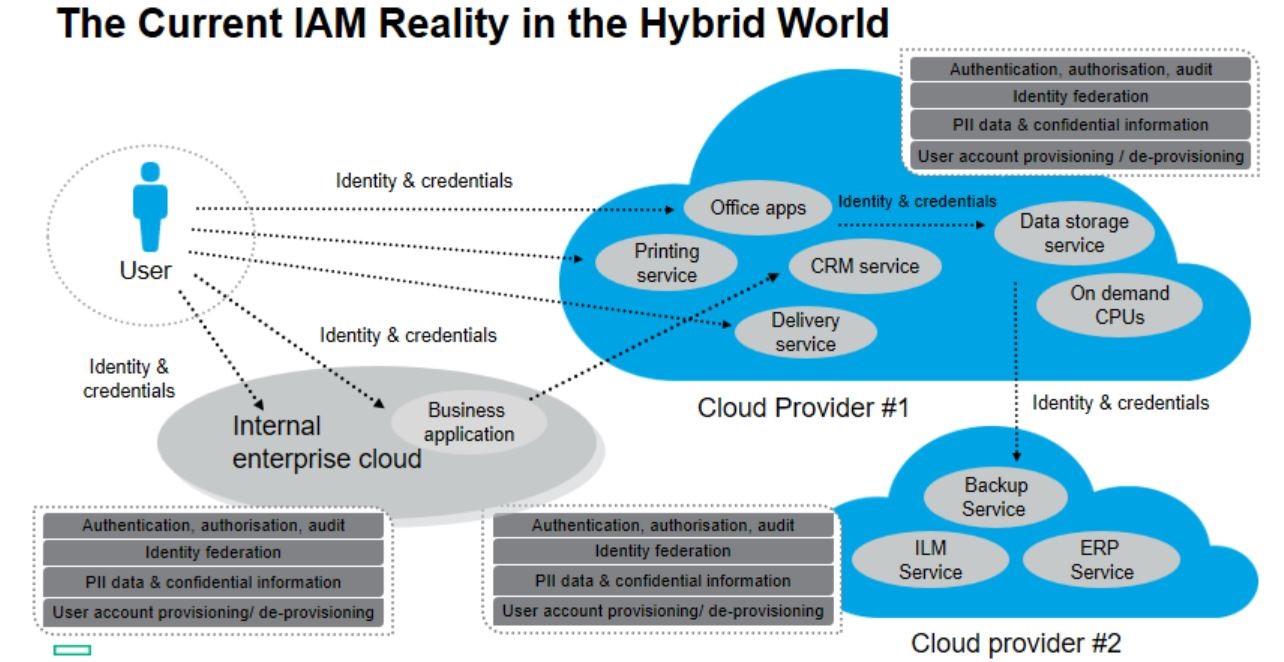
Identity Access Management in Cloud Computing
Cloud computing has revolutionized the way businesses operate, offering scalability, flexibility, and cost-efficiency. However, with the convenience of cloud services comes the challenge of securing sensitive data and ensuring only authorized users have access to resources.
Identity Access Management (IAM) plays a crucial role in addressing these security concerns in cloud computing environments. IAM involves managing digital identities and controlling access to resources based on user roles and permissions.
In cloud computing, IAM helps organisations enforce security policies, streamline user access management, and mitigate the risk of unauthorised access or data breaches. By implementing IAM frameworks, businesses can ensure that only authenticated and authorised individuals can access specific applications or data stored in the cloud.
Key components of IAM in cloud computing include authentication, authorisation, and accountability. Authentication verifies the identity of users through credentials such as passwords, biometrics, or multi-factor authentication. Authorisation determines what resources users can access based on their roles and permissions. Accountability ensures that all user activities are logged and monitored for security purposes.
Effective IAM implementation requires a comprehensive strategy that aligns with an organisation’s security policies and regulatory requirements. It involves defining user roles, setting up access controls, implementing encryption mechanisms, and regularly auditing user privileges to prevent insider threats or unauthorised access attempts.
By leveraging IAM solutions tailored for cloud environments, businesses can strengthen their security posture, enhance compliance with data protection regulations, and safeguard sensitive information from cyber threats. IAM not only enhances security but also improves operational efficiency by simplifying user management processes and reducing the risk of data breaches.
In conclusion, Identity Access Management is a critical aspect of securing cloud computing infrastructure. By adopting robust IAM practices and technologies, organisations can protect their data assets while enabling secure collaboration and innovation in the digital era.
Understanding Identity Access Management: Key Concepts and Importance in Cloud Computing
- What are the 4 pillars of IAM?
- Why is identity access management important for cloud computing?
- What are the 4 A’s of IAM?
- What is identity and access management for cloud resources?
- What is identity and access management in cloud?
What are the 4 pillars of IAM?
In the realm of Identity Access Management (IAM) in cloud computing, the concept of the “4 pillars of IAM” refers to the fundamental components that form the foundation of a robust identity and access management framework. These pillars include authentication, authorisation, accountability, and assurance. Authentication involves verifying the identity of users accessing resources through various methods such as passwords or biometrics. Authorisation determines what actions users are allowed to perform based on their roles and permissions. Accountability ensures that all user activities are tracked and audited for security purposes. Lastly, assurance focuses on maintaining trust in the IAM system by implementing security measures to protect against threats and vulnerabilities. By understanding and implementing these 4 pillars effectively, organisations can enhance their security posture and safeguard their sensitive data in cloud environments.
Why is identity access management important for cloud computing?
Identity access management (IAM) is crucial for cloud computing due to the dynamic and distributed nature of cloud environments. In the cloud, data and applications are accessed remotely from various locations and devices, increasing the complexity of managing user access. IAM ensures that only authorised individuals can access specific resources, reducing the risk of data breaches and unauthorised activities. By implementing IAM in cloud computing, organisations can enforce security policies, protect sensitive information, and maintain compliance with regulatory requirements. IAM enhances overall security posture by providing granular control over user permissions, authentication mechanisms, and monitoring capabilities, thereby safeguarding critical assets in the cloud ecosystem.
What are the 4 A’s of IAM?
In the realm of Identity Access Management (IAM) in cloud computing, the concept of the “4 A’s” refers to Authentication, Authorisation, Accountability, and Assurance. These four pillars form the foundation of a robust IAM framework that ensures secure access control and governance over digital resources in cloud environments. Authentication verifies the identity of users seeking access, while Authorisation determines their permissions based on predefined roles. Accountability involves monitoring and logging user activities for audit trails, and Assurance focuses on ensuring compliance with security policies and regulatory standards. Understanding and implementing these 4 A’s is essential for effective IAM practices in cloud computing to enhance data protection and mitigate security risks.
What is identity and access management for cloud resources?
Identity and access management for cloud resources refers to the practice of controlling and securing user identities and their access to data, applications, and services within a cloud computing environment. It involves managing user authentication, authorisation, and permissions to ensure that only authorised individuals can access specific resources based on their roles and responsibilities. By implementing robust identity and access management protocols in the cloud, organisations can enhance security, prevent data breaches, and maintain compliance with regulatory requirements. This proactive approach helps businesses protect sensitive information while enabling efficient and secure access to cloud resources for authorised users.
What is identity and access management in cloud?
Identity and Access Management (IAM) in cloud computing refers to the process of managing digital identities and controlling access to cloud resources. In essence, IAM ensures that only authenticated and authorised individuals can access specific applications or data stored in the cloud. By implementing IAM frameworks, organisations can enforce security policies, streamline user access management, and reduce the risk of unauthorised access or data breaches in the cloud environment. IAM encompasses authentication, authorisation, and accountability mechanisms to verify user identities, control resource access based on roles and permissions, and monitor user activities for security purposes.